Problem Statement
Standing permissions and persistent credentials in Azure are among the leading causes of cybersecurity breaches, unauthorized access, and compliance violations. Static access methods create an ever-present risk of exploitation, often resulting in costly security incidents.
The solution? Just-In-Time (JIT) Ephemeral Access—a security model that grants access only when needed and for a limited time. Although Azure Privileged Identity Management (PIM) provides a solution for JIT access, it is complex and does not operate in hybrid or multi-cloud scenarios.
Britive Approach
Britive SaaS JIT solution offer a simple, seamless, policy-driven workflow that eliminates the risks associated with Azure standing permissions. With Britive, organizations can achieve JIT ephemeral access that integrates effortlessly into their existing Azure environments.
Flexible Operating Models with Britive
Britive’s JIT ephemeral access can be achieved through multiple methods, tailored to fit diverse operational needs:
- User Interface (UI): Ideal for administrators and users who prefer an intuitive graphical interface.
- Command Line Interface (CLI): Designed for developers and DevOps engineers.
- Terraform (Programmatic): Perfect for integrating JIT access into CI/CD pipelines, enabling automated and scalable ephemeral permissions as part of your DevOps workflows.
JIT Checkout Workflow
Steps
- Login to https://portal.azure.com/
- Make sure you have selected the right Entra directory. In my case it is called “Britive Azure Test”
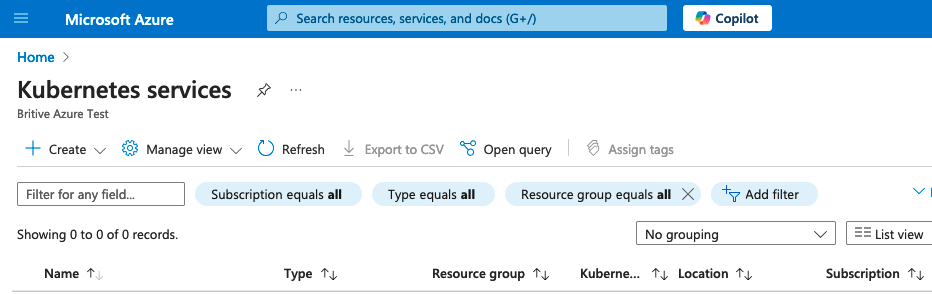
- Click subscription and notice your access is “Reader” or “read-only” for the subscription
- Click Azure Kubernetes services or other services and notice you don’t have any access
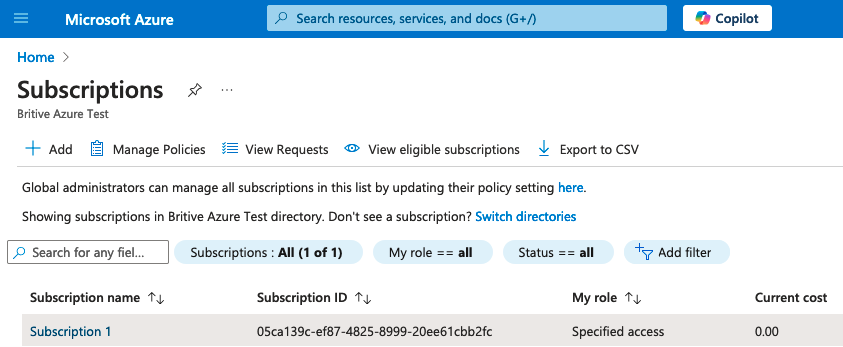
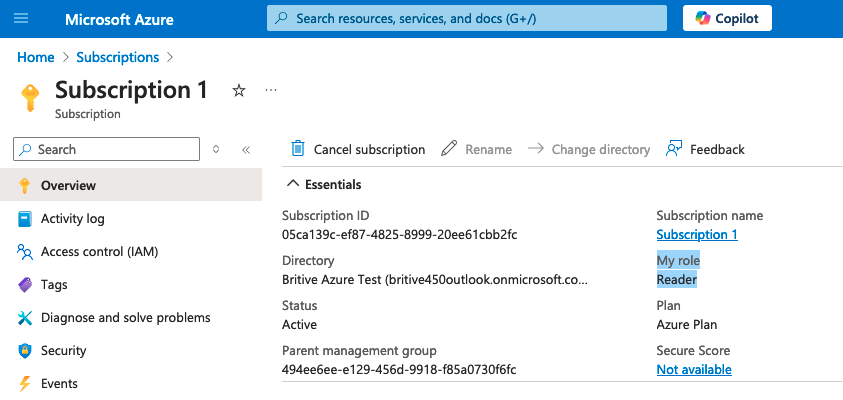
Read-Only Role
- Login to Britive console: https://demo.britive-app.com/my-access
- Checkout profiles called “Azure Global Admin and “Azure Subscription Owner”
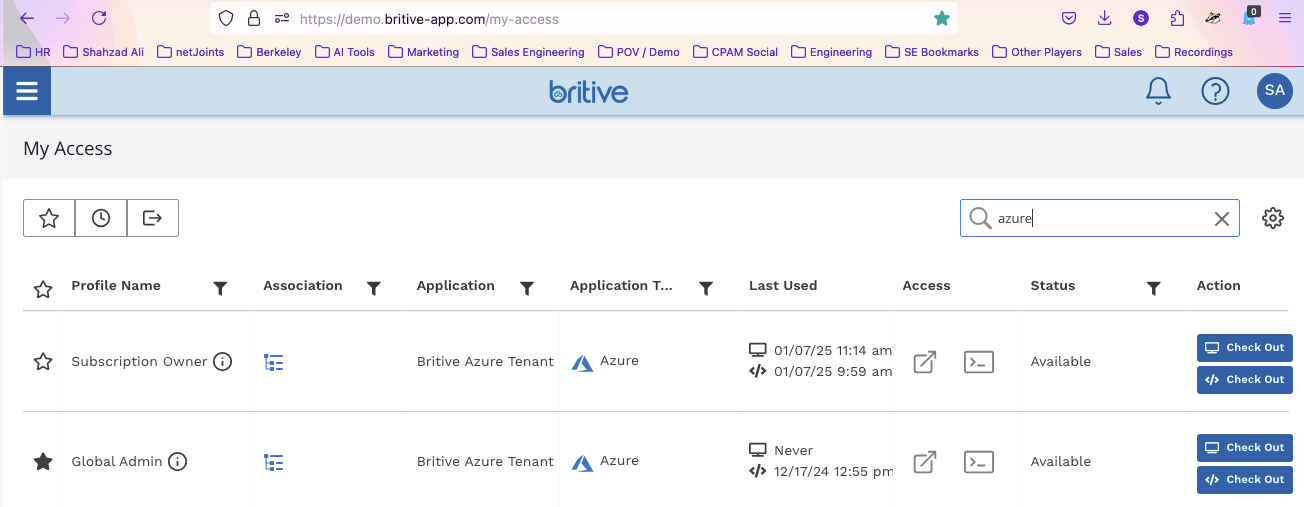
As soon as “Azure Global Admin” is checked out, you will receive an email from Entra ID as well.
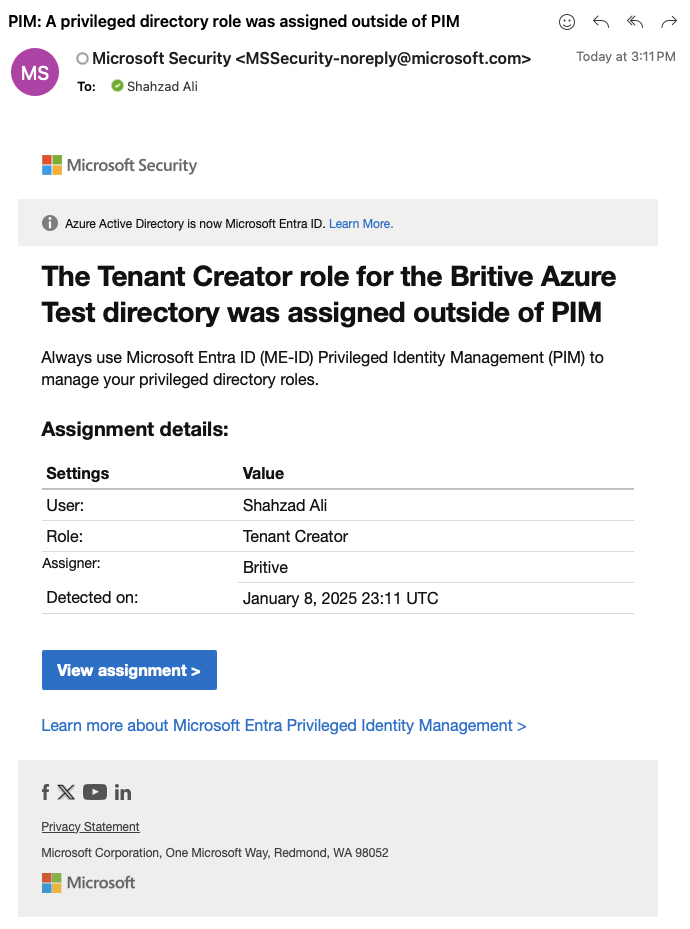
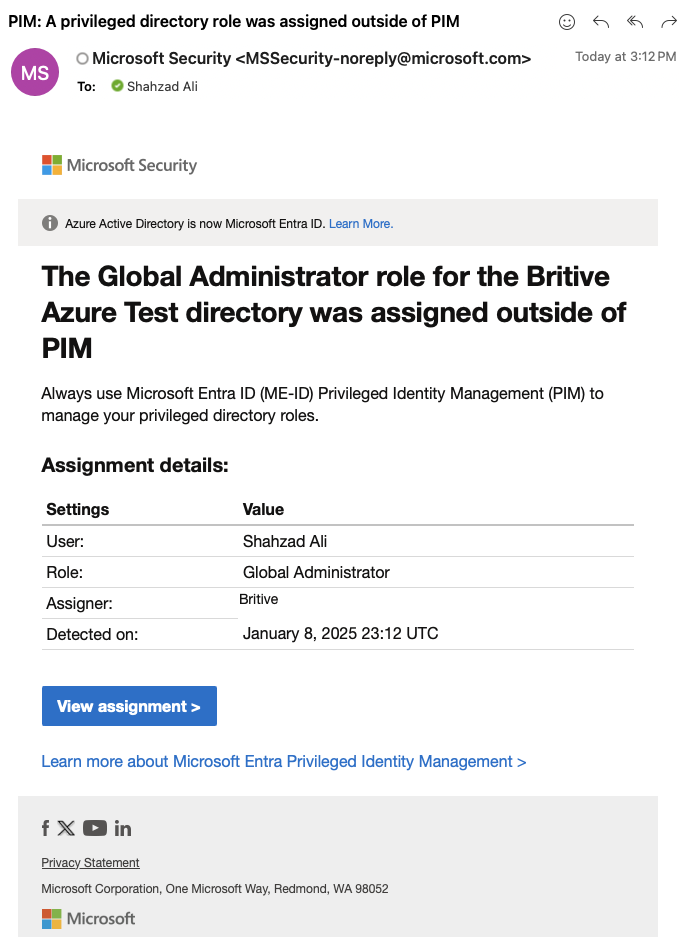
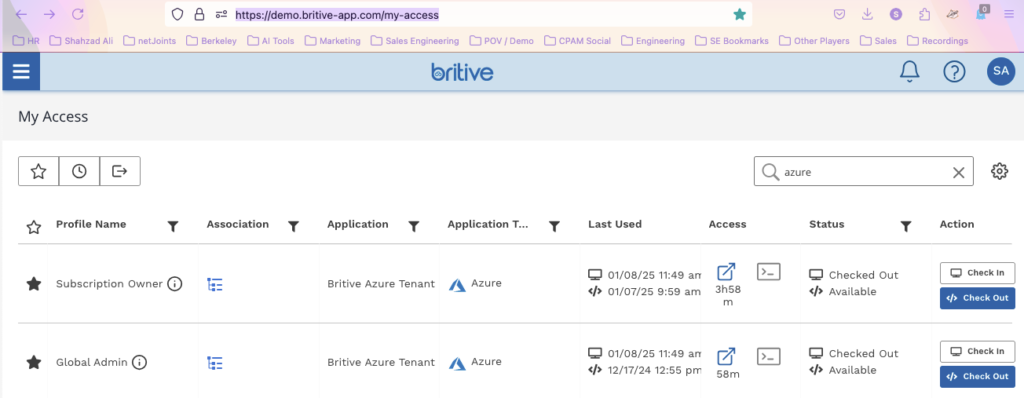
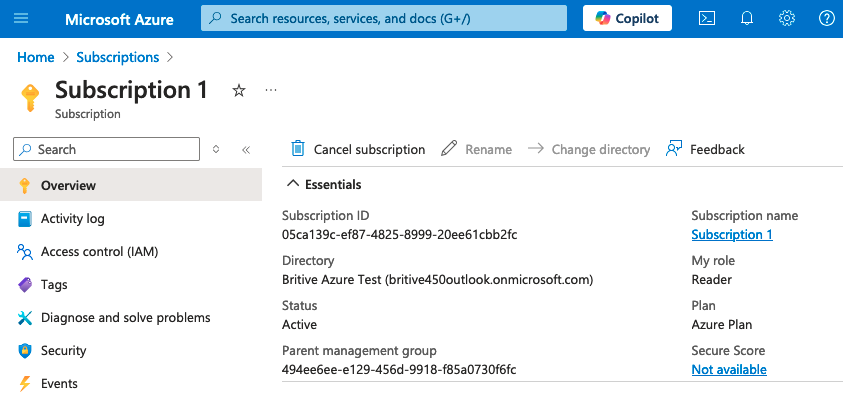
Now you should be able to see subscription and other details
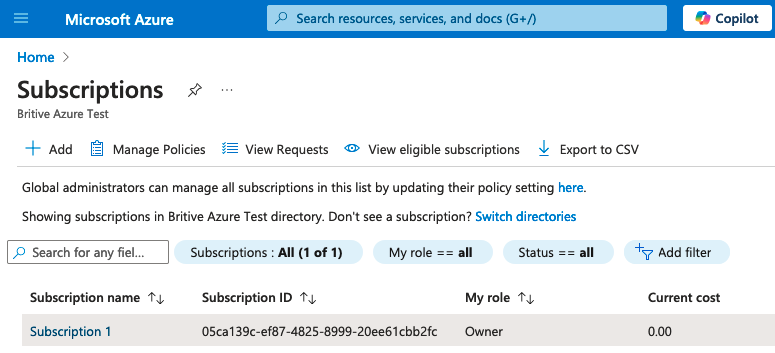
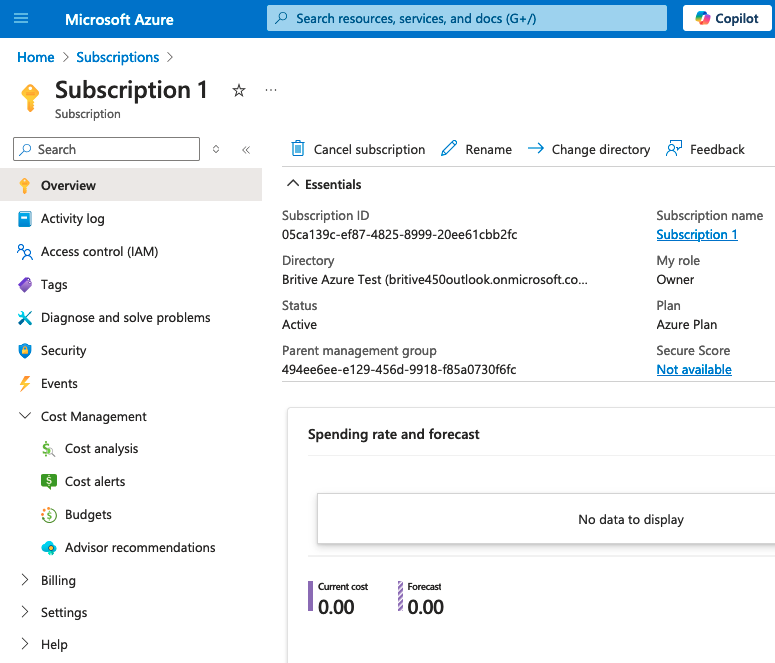
In the following diagram notice that my Azure role is changed to “Owner” now.
JIT Checking
Use can manually checkin the JIT permission or a time bound activity will automatically check those permission in so now the user will go back to read-only owner mode again
Conclusion
In conclusion, by leveraging Britive’s Just-In-Time (JIT) ephemeral access, organizations can significantly reduce the risks associated with standing permissions. Workloads, applications, and infrastructure are now more secure, with access granted only when necessary and within defined policy constraints.
This approach not only enhances security but also aligns with modern compliance and operational best practices.
Sounds too good to be true? Send Britive a live demo request to see it in action here: https://www.britive.com/contact
Comments are closed