Understanding IAM Conditions in Google Kubernetes Engine (GKE)
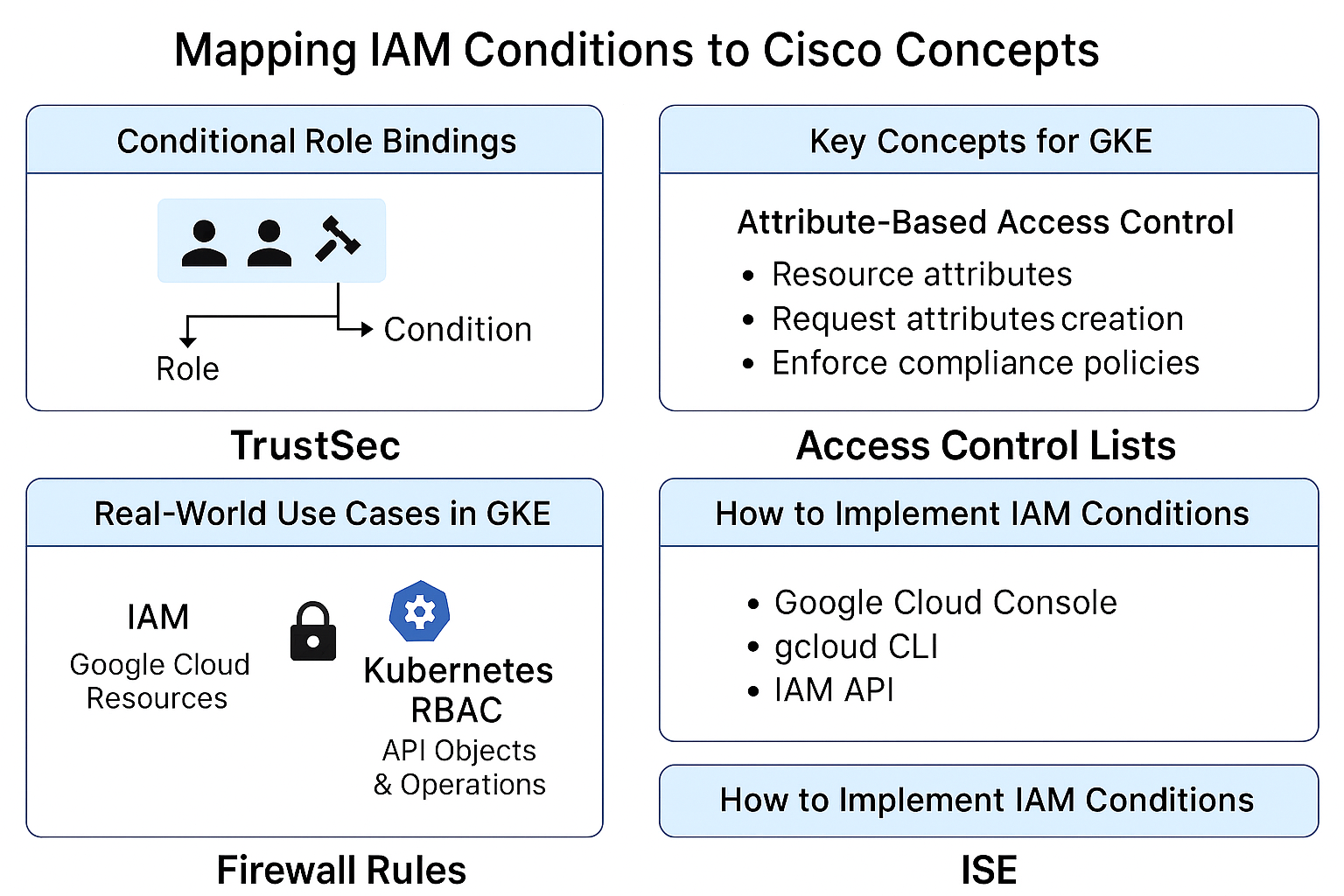
Think of IAM Conditions in GKE like access control lists (ACLs) or firewall rules in Cisco networking but for cloud resources. They allow you to define very specific rules about who can do what, where, and when in your Google Cloud environment.
What Are IAM Conditions?
IAM (Identity and Access Management) Conditions are part of Google Cloud’s security model. They let you grant roles to users or service accounts only if certain conditions are met. Similar to how you might allow traffic through a router only if it matches a specific IP, protocol, or time window.
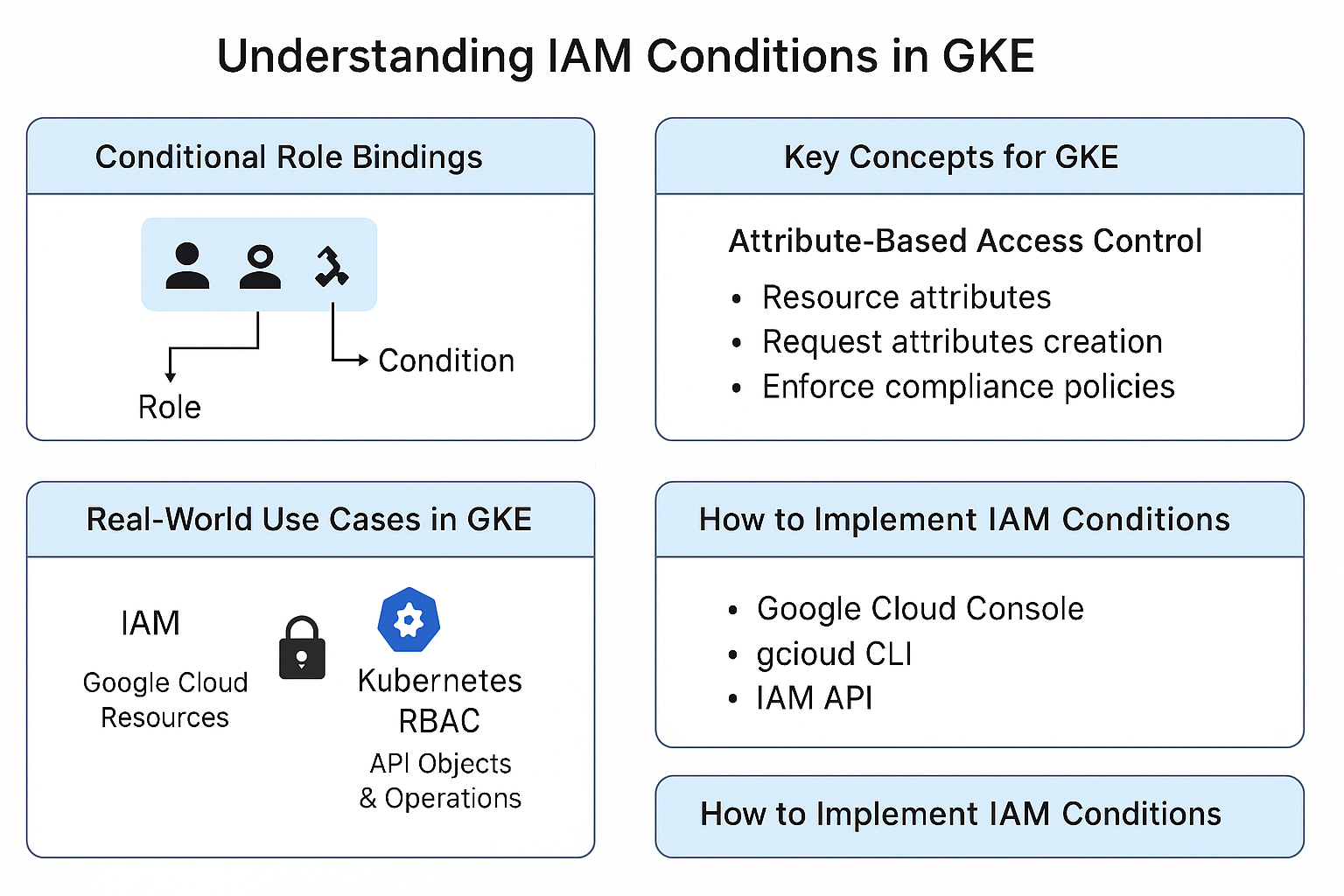
Key Concepts for GKE (Google Kubernetes Engine):
Conditional Role Bindings
- You assign roles (like “Cluster Admin”) to users or service accounts.
- But the role is only active if the condition is true — like saying “allow access only if the request comes from a specific IP range.”
Attribute-Based Access Control (ABAC)
Conditions can be based on:
- Resource attributes: e.g., only allow access to clusters named
prod-*or located inus-central1. - Request attributes: e.g., allow actions only during business hours or only for
createoperations. - Principal attributes: e.g., allow access only if the request comes from a known IP or a specific service account.
Real-World Use Cases in GKE:
- Restrict access to specific clusters
Like limiting access to only production clusters, not dev or test. - Control load balancer creation
Prevent external load balancers from being created — only allow internal ones. - Enforce compliance policies
Ensure sensitive actions (like deleting clusters) can only happen under strict conditions.
How IAM Conditions Work with Kubernetes RBAC
- IAM controls access to Google Cloud resources (like the GKE cluster itself).
- Kubernetes RBAC controls access inside the cluster (like pods, services, etc.).
- Together, they provide end-to-end security — like combining perimeter firewall rules with internal ACLs.
How to Implement IAM Conditions
- Conditions are written using CEL (Common Expression Language) — similar to writing firewall match conditions.
- You can configure them via:
- Google Cloud Console
- gcloud CLI
- IAM API
Cisco Analogy Diagram
Comments are closed