Abstract
Agentic AI is shifting from experiments to production, and the Model Context Protocol (MCP) is quickly becoming the adapter layer that allows autonomous agents to access tools, data, and workflows. This paper distills current MCP security practices, spanning specification features (OAuth 2.1, discovery and resource indicators), implementation controls (JIT/ZSP, schema validation, observability), and operational hardening, to help teams move beyond demos with confidence.
Introduction
Autonomous AI agents now execute tasks across databases, SaaS applications, and internal APIs. MCP provides a unified way to expose these resources to agents, but with that flexibility comes risk: MCP servers often handle credentials, tool calls, and business logic, making them central to the agentic control plane and prime targets for misuse or compromise.
While the MCP specification has evolved to include OAuth 2.1 and security best practices, runtime authorization and enforcement remain the implementer’s responsibility.
The enterprise reality: Interoperability accelerates adoption, which expands the attack surface. Hardening MCP servers and governing agent access at runtime becomes essential for safe scale.
As organizations rapidly adopt AI agents powered by Large Language Models, a critical security challenge has emerged: how do we safely grant autonomous systems access to enterprise resources? The Model Context Protocol has become the de facto standard for connecting AI agents to external tools and data, yet its initial specification left significant security gaps. This whitepaper examines the architecture of MCP-based agentic systems, identifies key vulnerability vectors, and presents a comprehensive framework for implementing runtime access controls that enable innovation while maintaining security posture.
What Is MCP and Why It Matters for Agentic AI
Model Context Protocol represents a paradigm shift in how AI systems interact with enterprise infrastructure. Introduced by Anthropic in late 2024, MCP provides a standardized communication layer between Large Language Models and external services, solving what the industry refers to as the “N×M problem”—the exponential complexity of integrating N different LLMs with M different data sources without a universal protocol.
MCP Architecture in Brief
MCP operates through three core components that establish a clear separation of concerns. The MCP Host serves as the user-facing application layer where humans interact with AI agents. This includes applications like Claude Desktop, Cursor IDE, or custom agentic interfaces. The MCP Client acts as the protocol adapter, translating LLM requests into standardized MCP messages and managing connections to multiple servers. Finally, the MCP Server exposes specific tools and resources, handling authentication, authorization, and actual execution of operations against target systems.
MCP follows a Host–Client–Server pattern: the Host coordinates agent sessions and security boundaries, the Client brokers protocol messages and tool invocation, and the Server exposes tools/resources and context. The result is an interoperable layer that simplifies agent integration across multiple tools and models.
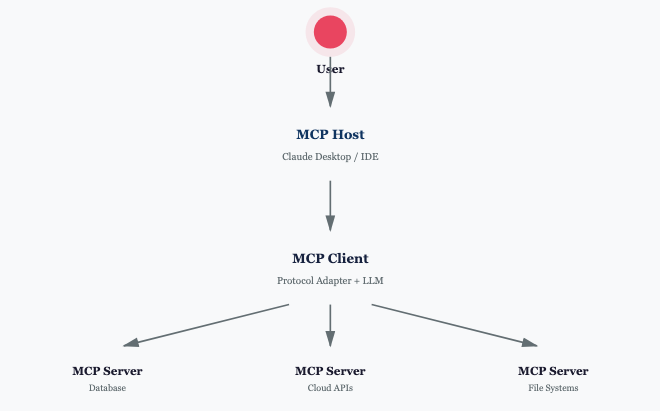
This architecture creates natural security boundaries. Each layer can implement controls independently: the host determines which servers to trust, the client manages credential flows, and servers enforce resource-level authorization. However, the protocol’s flexibility also introduces risk. Without proper safeguards, compromised components can cascade failures across the entire system.
The Rapid Rise of MCP in the Enterprise
MCP adoption is accelerating across vendors and enterprises, creating a mainstream integration fabric for agentic systems—and a new, largely unseen attack surface if not governed. Visibility, policy, and least‑privilege controls are now table stakes.
The Security Gap in MCP Specifications
The initial MCP specification prioritized interoperability over security, leaving several critical concerns unaddressed. Authentication mechanisms were loosely defined, with many implementations defaulting to hardcoded credentials or environment variables—a practice that contradicts modern zero-trust principles. Authorization granularity was limited, typically operating at the server level rather than per-tool or per-resource. Audit trails and compliance logging were not standardized, making it difficult to track which AI agents accessed what data and when.
Security Reality Check
According to Verizon's Data Breach Investigations Report, credential compromise accounts for approximately 80% of breaches. As MCP adoption accelerates, each AI agent becomes a potential attack vector if not properly secured with dynamic access controls.
Threat Model | What Can Go Wrong with MCP Servers
AI‑Native Attack Vectors
Prompt injection and tool poisoning can trick models into issuing harmful tool calls or exfiltrating data. Studies and case reports show how malicious tool metadata or cleverly crafted instructions can hijack agent behavior. Command/code injection becomes possible if untrusted inputs reach shells, SQL engines, or interpreters without strict validation.
Protocol/Authorization Pitfalls
The confused deputy problem arises in MCP proxy flows, especially when a static OAuth client ID is reused against third-party authorization servers. Overbroad scopes or token passthrough can turn an access token into a “skeleton key” unless tokens are properly bound and intent-aware controls exist.
The State of MCP Security | Spec vs. Reality
The MCP specification now references OAuth 2.1 for protected resource access with authorization server discovery (PRM / RFC 9728), dynamic client registration (RFC 7591), and resource indicators (RFC 8707) to bind tokens to specific servers. Security best practices address consent UI, cookie hardening, CSRF, and redirect URI validation—especially in proxy scenarios.
What You Still Need to Implement
Spec features are necessary but insufficient: you still need defense‑in‑depth (network isolation, identity, authorization, validation, observability) and runtime enforcement that adapts to agent intent and task context. Real-time authorization and least privilege are operational requirements, not protocol defaults.
| Spec Features | Operational Control / Why It Matters |
|---|---|
| OAuth 2.1 | Add runtime AuthZ, Approvals |
| PRM (RFC 9728) | Secure Discovery |
| DCR (RFC 7591) | Lock URIs, per client consent |
| Resource Indicators | Bind tokens to servers |
| Best Practices | Consent UI, cookies, CSRF |
Designing a Secure MCP Server | Reference Architecture
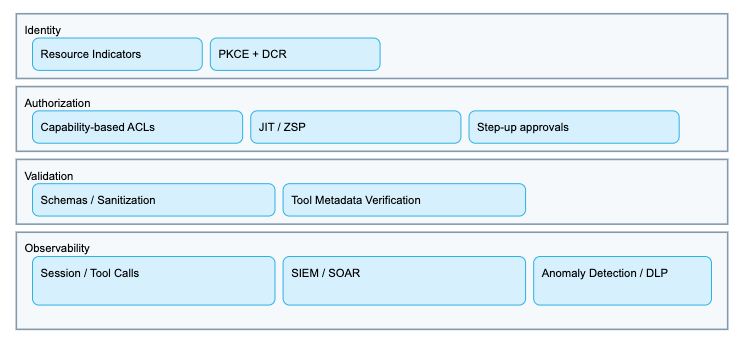
Control Layers (Edge to Tool)
- Network & traffic mediation: API gateway, mTLS, and zero‑trust proxies; local binding in dev, strict ingress in prod.
- Authentication/Authorization: OAuth 2.1 with PKCE and resource indicators; capability‑based ACLs; per‑task least privilege.
- Input/Output validation: strict schemas, normalization, and output sanitization to mitigate injection.
- Secrets & credential hygiene: eliminate hard‑coded secrets; time‑bound credentials with auto‑expiry; rotate and revoke aggressively.
- Observability: full audit trail of agent sessions, tool calls, approvals, and revocations; SIEM/SOAR integration.
Policies That Match Agentic Behavior
Implement just‑in‑time (JIT) access for non‑human identities and zero standing privileges (ZSP) so agents receive the minimum permissions needed, only when needed, and checked back in automatically. Use step‑up approvals and revocation for sensitive operations.
Operational Hardening & Governance for MCP
Foundational Hygiene (Still Wins)
Most breaches are preventable with baseline hygiene: secure coding, supply chain integrity, dependency vetting, and sound configuration practices—these apply equally to AI stacks. Combine runtime isolation (containerization, sandboxing) with version management and backup/DR for server configs and prompts.
Continuous Visibility & Policy Enforcement
Inventory all MCP servers/clients; monitor non‑human traffic and prompt behavior; apply default‑deny for MCP traffic where appropriate; integrate risk scoring and DLP to prioritize remediation and prevent leakage of IP or credentials in agent workflows.
Inventory all MCP servers/clients; monitor non‑human traffic and prompt behavior; apply default‑deny for MCP traffic where appropriate; integrate risk scoring and DLP to prioritize remediation and prevent leakage of IP or credentials in agent workflows.
MCP Security Playbook—Step‑by‑Step Implementation
1) Establish Trust Boundaries
Map where hosts/clients/servers run; bind tokens to specific resources with resource indicators; harden consent and exact URI matching for redirects; protect cookies (Secure, HttpOnly, SameSite) and implement CSRF controls.
2) Enforce Identity & Access at Runtime
Use JIT/ZSP for agents; provision time‑bound credentials per task; auto‑expire and check in access; apply step‑up authentication for elevated actions.
3) Validate Tools & Sanitize I/O
Verify tool metadata and watch for dynamic capability changes; enforce strict input schemas and output sanitization to prevent SQL/command injection; treat model‑generated content as untrusted input.
4) Observe, Log, and Respond
Log sessions, tool calls, elevation requests and revocations; stream to SIEM/SOAR; detect anomalies in agentic behavior and block suspicious flows in real time.
Looking Ahead—The Ecosystem & Emerging Tooling
Security tooling around MCP is expanding. Community hubs (CSA’s MCP Security Resource Center) consolidate hardening guidance, while vendors introduce capabilities to discover MCP servers/clients, inspect MCP traffic, score risk, and enforce policy for agentic sessions as they move into production. This reflects a broader shift toward runtime guardrails designed for AI-native workflows.
Conclusion
Bottom line: MCP is becoming the switchboard for agentic AI. The spec’s OAuth 2.1 foundation is necessary, but enterprises must add defense‑in‑depth, runtime least privilege (JIT/ZSP), strict validation/sanitization, and robust observability. Start with trust boundaries, eliminate static secrets, bind tokens to servers, and enforce context‑aware authorization to keep agent autonomy aligned with business intent
References (for editorial linking)
- MCP Spec — Security Best Practices (confused deputy, consent, cookies, URI validation). [modelconte…rotocol.io]
- Microsoft Security Guidance (MCP risks & baseline hygiene). [techcommun…rosoft.com]
- GitHub Blog (secure/scalable remote MCP servers; PRM, DCR, resource indicators). [github.blog]
- CSA MCP Security Resource Center (hardening guidance). [cloudsecur…liance.org]
- Pomerium (Zero Trust enforcement for MCP; need for continuous authorization). [pomerium.com]
- Ecosystem coverage (discovery, policy, risk scoring for MCP traffic). [netskope.com]
- Agentic identity runtime controls & evidence trails (operational examples of JIT/ZSP for non‑human identities). [msspalert.com]
- Technology illustrations by Storyset
Comments are closed