Scenario
ABC Healthcare (a fictitious company), a leading healthcare provider, operates solely within the AWS cloud environment. For their internet egress traffic, they rely on AWS NAT Gateway. While AWS NAT Gateway serves well for IP address translation, it’s not designed to be a robust security solution. This lack of dedicated security has raised concerns about data privacy and HIPAA compliance among ABC Healthcare’s management.
Expensive and Limited CSP Native NAT Gateway
The current AWS NAT Gateway doesn’t provide the necessary visibility and logging capabilities, and it’s also very expensive due to 2 cents per GB egress data processing charges. ABC Healthcare’s average monthly egress traffic is around 500 TB.
The native solution also lacks visibility, is cost-prohibitive, and doesn’t support zero trust architecture—putting sensitive patient data and the healthcare provider’s reputation at risk.
Data Charges Reference:
Damaged Reputation and Employee Fired
To further complicate matters, ABC Healthcare recently suffered a data exfiltration attack, leading to significant disruptions, reputational damage, and a negative impact on their stock value. This incident resulted in the dismissal of the previous cloud network architects.
You are the Newly Hired Cloud Networking Architect
You, the newly appointed architect, have been tasked with securing this traffic using the Aviatrix Secure Egress solution. Your mission is to implement a solution that enhances visibility, provides detailed logging, and complies with regulatory mandates while being cost-effective and efficient.
LAB Objective
Your job to do a POC/POV in your lab and demonstrate how your company can leverage Aviatrix Cloud Perimeter Solution to solve this pain point. You need to deploy the Aviatrix Secure Egress solution using Aviatrix Spoke Gateway to protect internet-bound traffic more effectively than with the native AWS NAT Gateway.
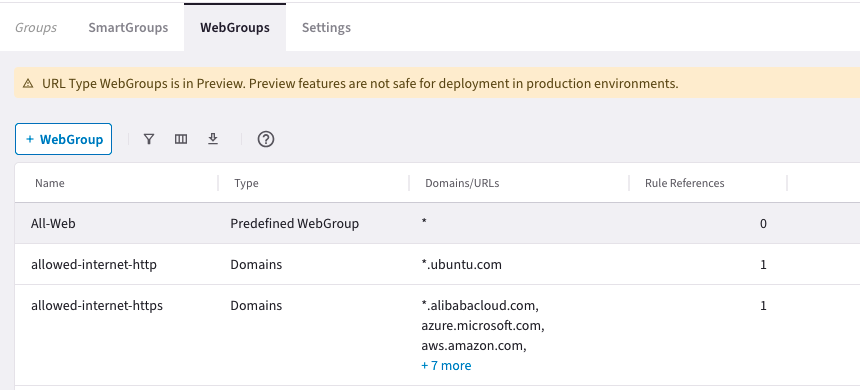
The Zero Trust policy should only allow following websites and block all other FQDNs.
The lab intentionally does not provide all the steps to you to complete this lab. You should leverage https://docs.aviatrix.com if you are stuck.
- allowed-internet-http domains
- *.ubuntu.com
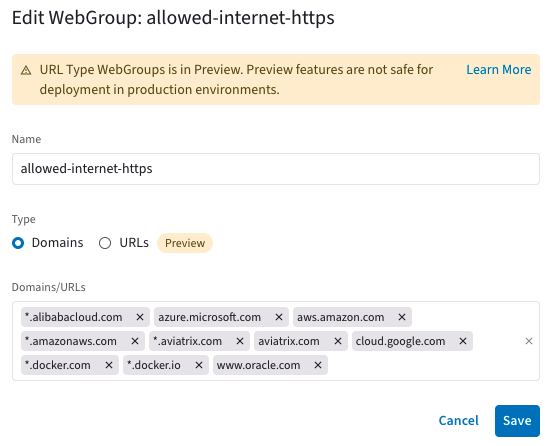
- allowed-internet-https domains
- *.alibabacloud.com
- azure.microsoft.com
- aws.amazon.com
- *.amazonaws.com
- *.aviatrix.com
- aviatrix.com
- cloud.google.com
- *.docker.com
- *.docker.io
- www.oracle.com
Listen to the following recording
Listen carefully there will be quiz questions based on this 4 min video too.
LAB Pre-Req
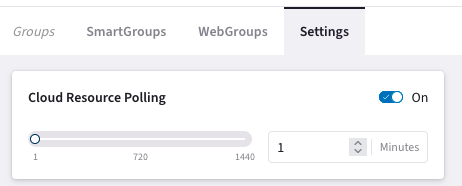
Before starting the lab, change the following timers to their lowest value
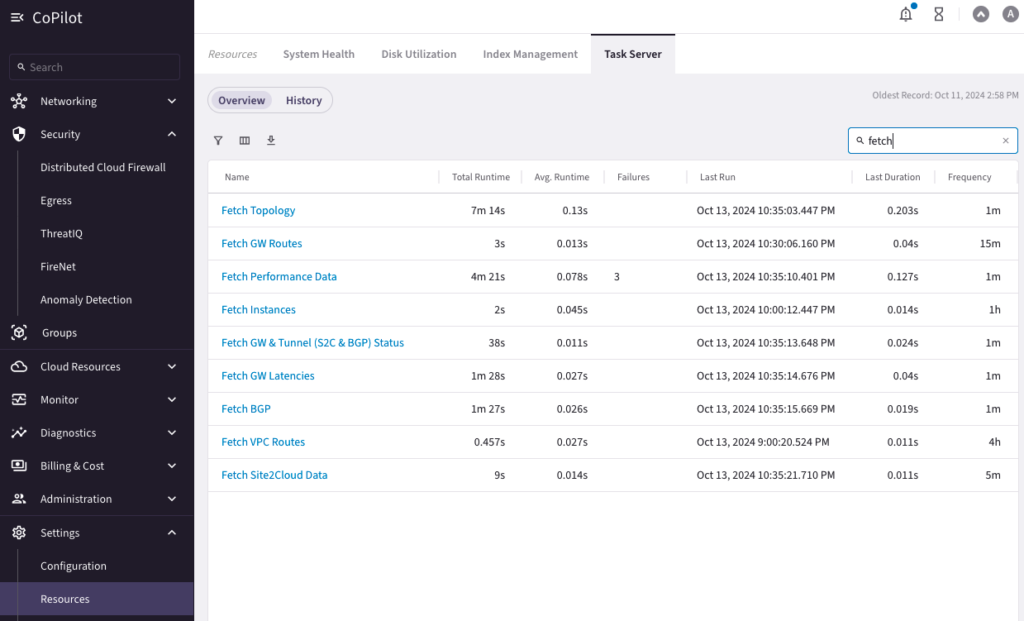
DO NOT ATTEMPT TO CHANGE THE FREQUENCY IN PRE-PROD or PROD SETUP. THIS WOULD CAUSE SERIOUS ISSUES.
It should look like the following
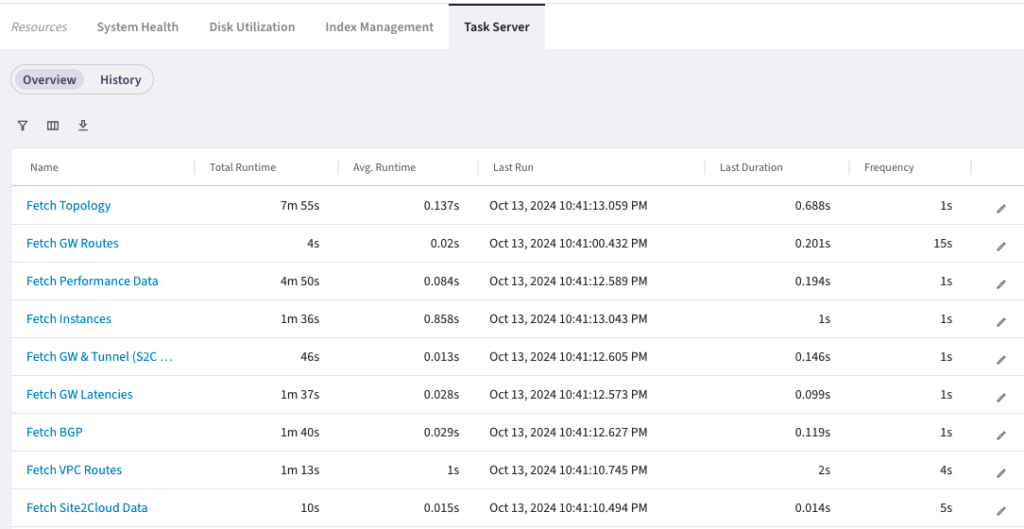
Do not change these frequencies in the production setup
- Aviatrix Spoke GW must be deployed in Region us-east-1 in the “egress-vpc”
- GW Instance Size should be t3a.small
Successful Completion of LAB
After completing the lab, your screen more or less should look like the following. The IP addresses and UUIDs could be different.
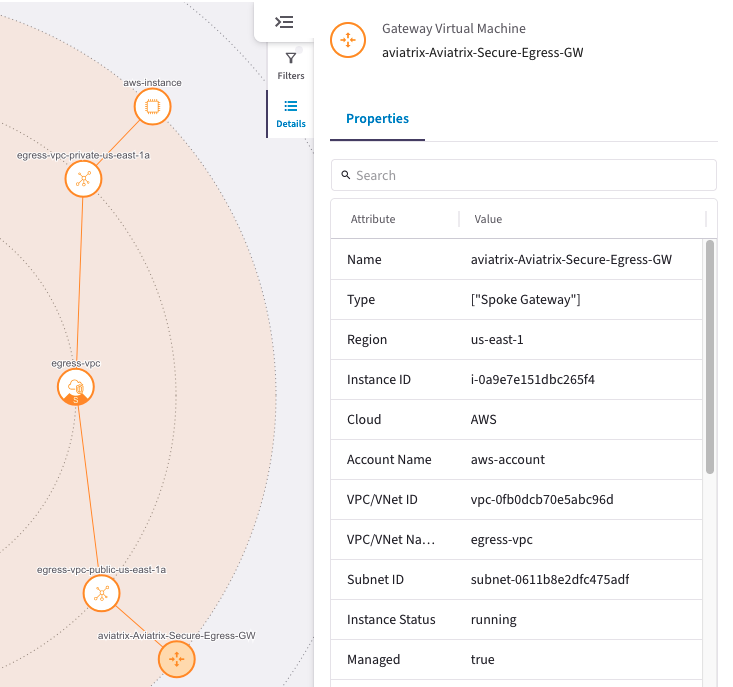
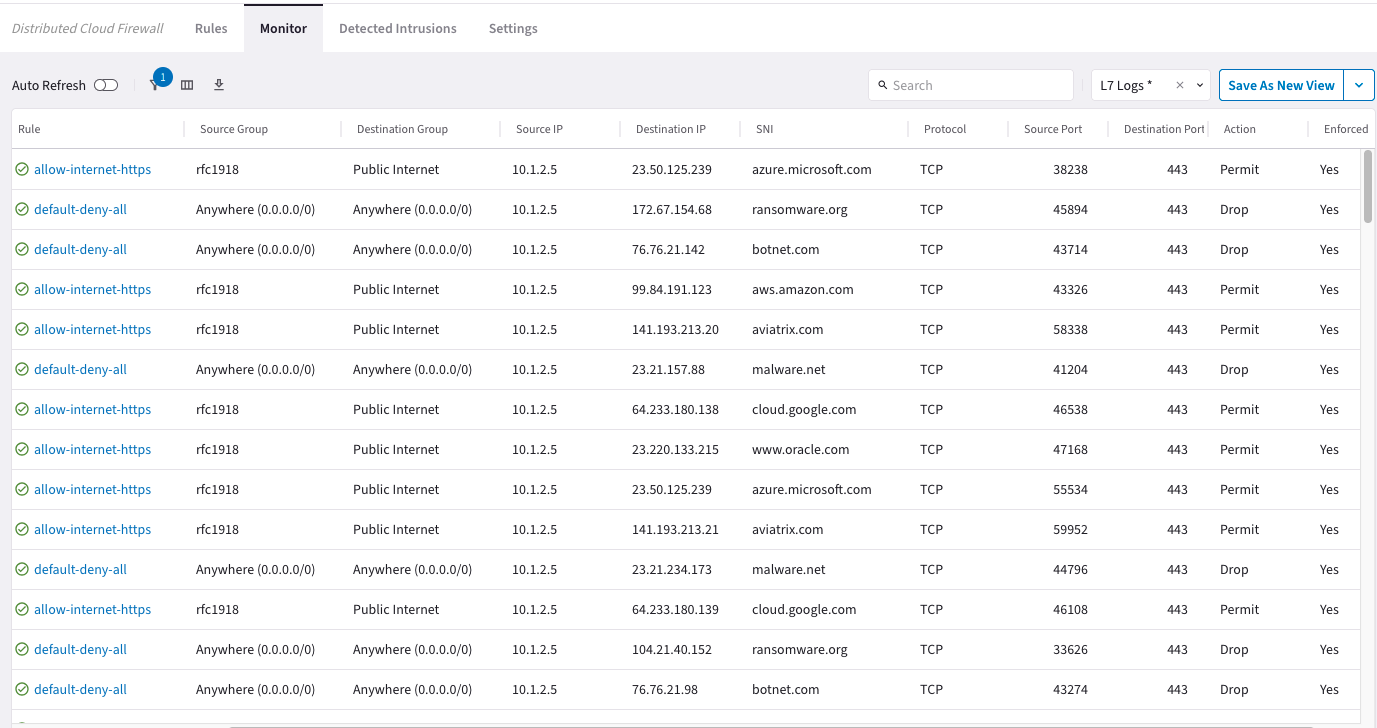
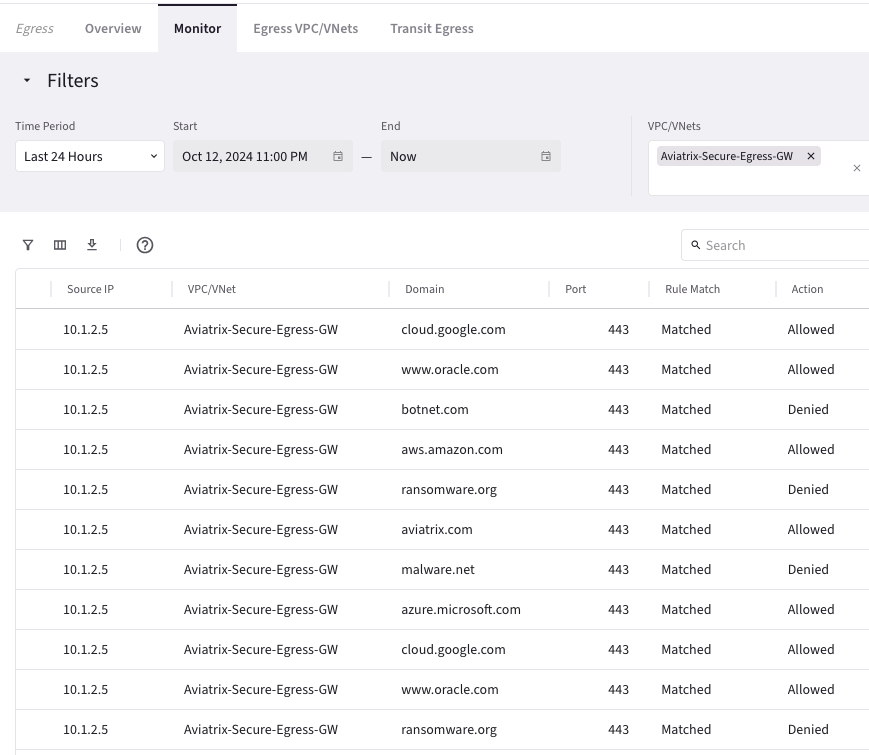
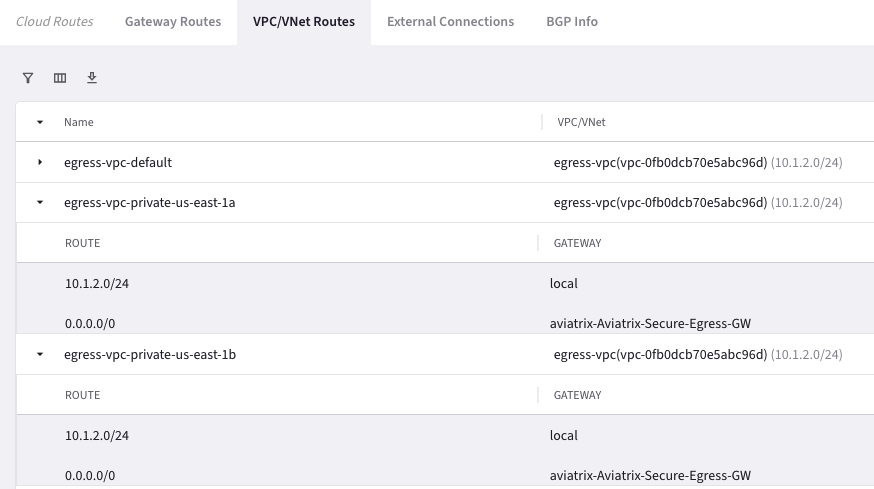
LAB HINTS
Create Secure Egress DCF Rules
- Create three rules
- The last DCF rule is a zero-trust rule
- Rule 100 is to allow traffic from the test instance on the private IP address to the public internet only to FQDNs specified in the “allowed-internet-https” web group
- Rule 0 is to allow traffic from the test instance on the private IP address to the public internet only to FQDNs specified in the “allowed-internet-http” web group
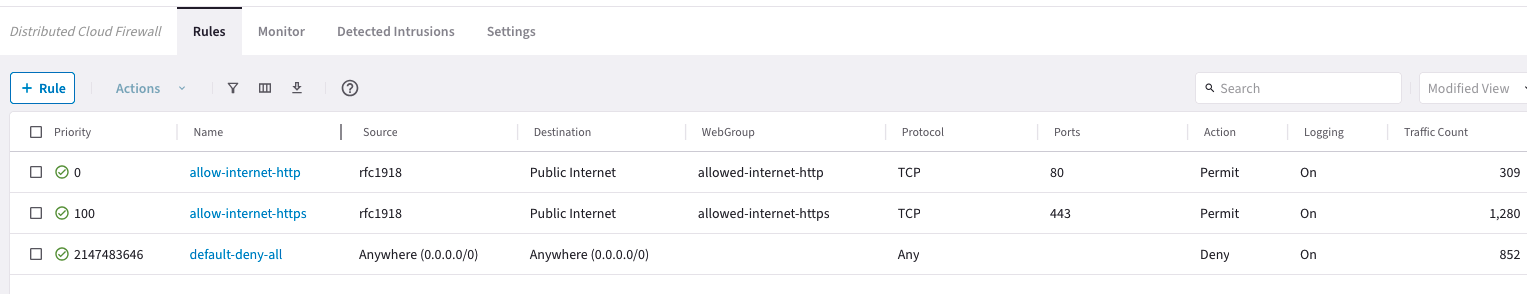
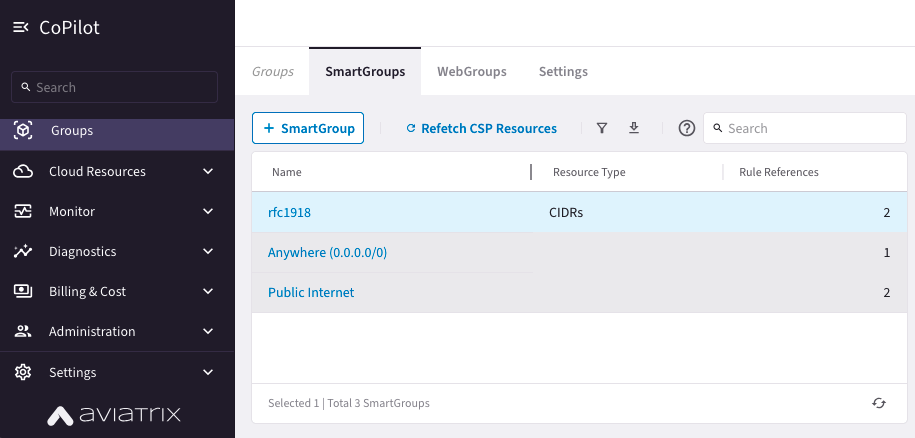
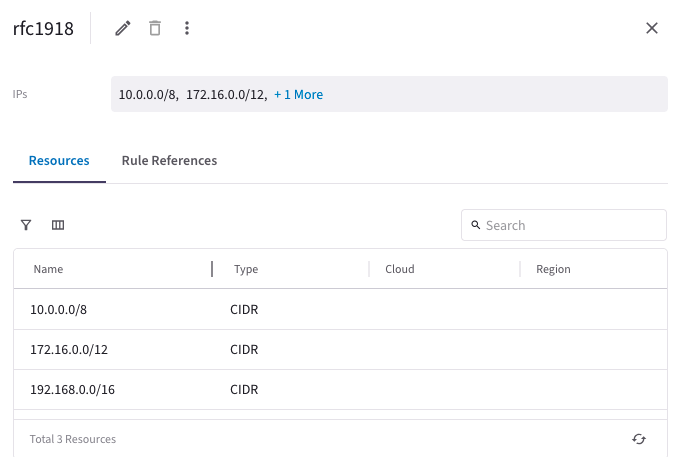
Create rfc1918 SmartGroup
Create WebGroup to Define FQDN Allowed to Access Internet
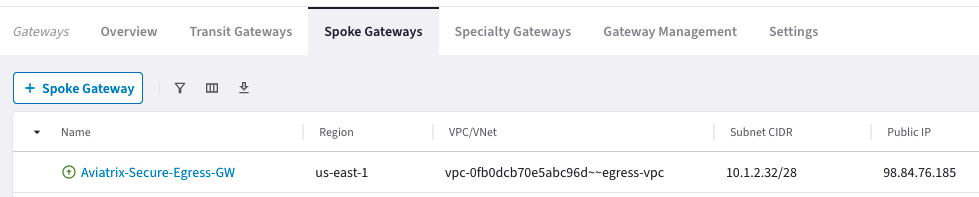
Deploy Aviatrix Spoke GW
- The public IP address will be different (Public EIP automatically allocated by CSP)
- The Subnet CIDR could be different (automatically picked up by Aviatrix Controller)
- Region: us-east-1
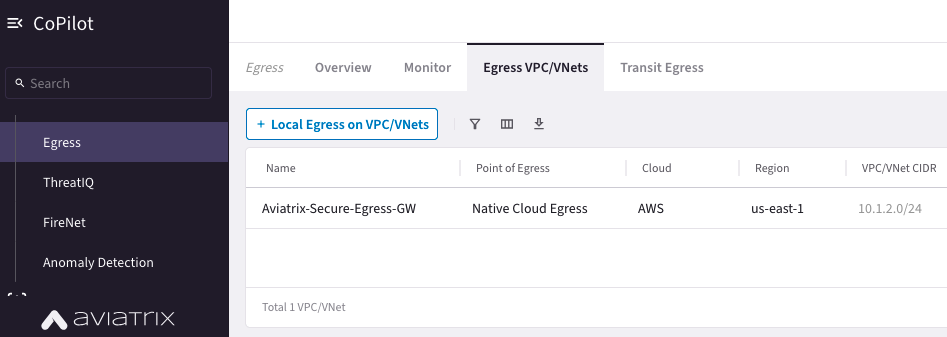
Check the Egress setting. The Egress traffic is going using the native NAT GW.
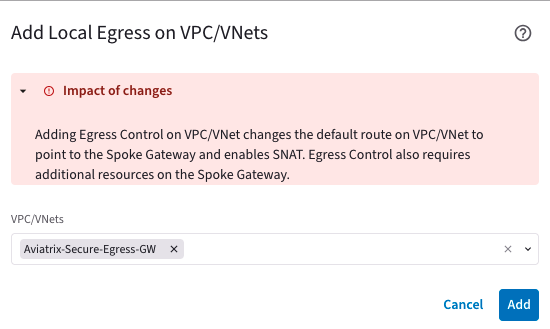
Enable spoke GW to become the Egress GW
- Click +Local Egress on VPC/VNets.
- In the Add Local Egress on VPC/VNets dialog, select the VPC/VNets on which to enable Local Egress.
- Click Add.
Read more at Aviatrix Documentation
Add Local Egress on VPC/VNets
Adding Egress Control on VPC/VNet changes the default route on VPC/VNet to point to the Spoke Gateway and enables SNAT. Egress Control also requires additional resources on the Spoke Gateway.VPC/VNets
Now the diagram should look the following
Conclusion
By bringing Aviatrix Secure Egress into play, our healthcare provider shored up their defenses, dropped the high costs, and eliminated the visibility black hole courtesy of the AWS NAT Gateway. Sensitive patient data is safe, and the provider’s reputation will be secured.
Remember, Aviatrix Secure Egress is your go-to for a secure, cost-effective solution for managing internet-bound traffic. Need more help? Our support team’s got your back.
Comments are closed