What is CIEM?
Cloud infrastructure entitlement management (CIEM) tools manage identities and privileges in cloud environments. CIEM tools scans cloud access control policies, rules and configurations. CIEM then present a report listing
- Which entitlement exist
- What each human or non-human (machine/service account) can do based on entitlements
- Which human and non-human users can access cloud resources based on entitlements

Rise of Multicloud and Associated Complexities
Legacy IAM tools provide access control to static self-hosted or on-premise infrastructure. These legacy tools don’t work in the cloud. The cloud infrastructure, services and applications are ephemeral and dynamic. So managing entitlements and access in single cloud itself is a challenge.
To further complicate the issues, lets add multi cloud in the mix. According to Gartner, 81% of organizations report working with two or more public cloud providers. Because public cloud providers don’t natively integrate, a multicloud strategy can find managing entitlements for each cloud environment broken.
CIEM tools gained popularity during 2020-2022 time frame as they, at least, provided reporting capabilities to help understand access and entitlements risks, across multi cloud environment.
Where CIEM Falls Short
CIEM reports the symptoms but Is NOT the Complete Solution
CIEM tools can identifying symptoms—they can generate reports on over-provisioned entitlements and flag outdated identities. However, CIEM tools cannot enforce the policy or cannot fix the problem.
CIEM tools are primarily focused on monitoring access activity and identifying issues, but they still require manual intervention to remediate problems. The underlying issue—the presence of standing permissions and excessive entitlements—remains unaddressed.
The Next Frontier: Ephemeral JIT CPAM
To truly solve the problem at its root, organizations need to move beyond CIEM. The next step is a Just-in-Time Ephemeral Multi-Cloud Privileged Access Management (JIT CPAM) solution. By eliminating standing entitlements and providing time-bound, dynamic access, JIT CPAM fixes the root cause and delivers secure, scalable access management across cloud environments.
Britive: The leader in Ephemeral JIT CPAM Category
Britive is leading the charge in addressing these challenges by going beyond traditional CIEM solutions. Britive offer fundamental and critical features expected from a CIEM tool. Lets explore those features one by one
Extensive Reporting
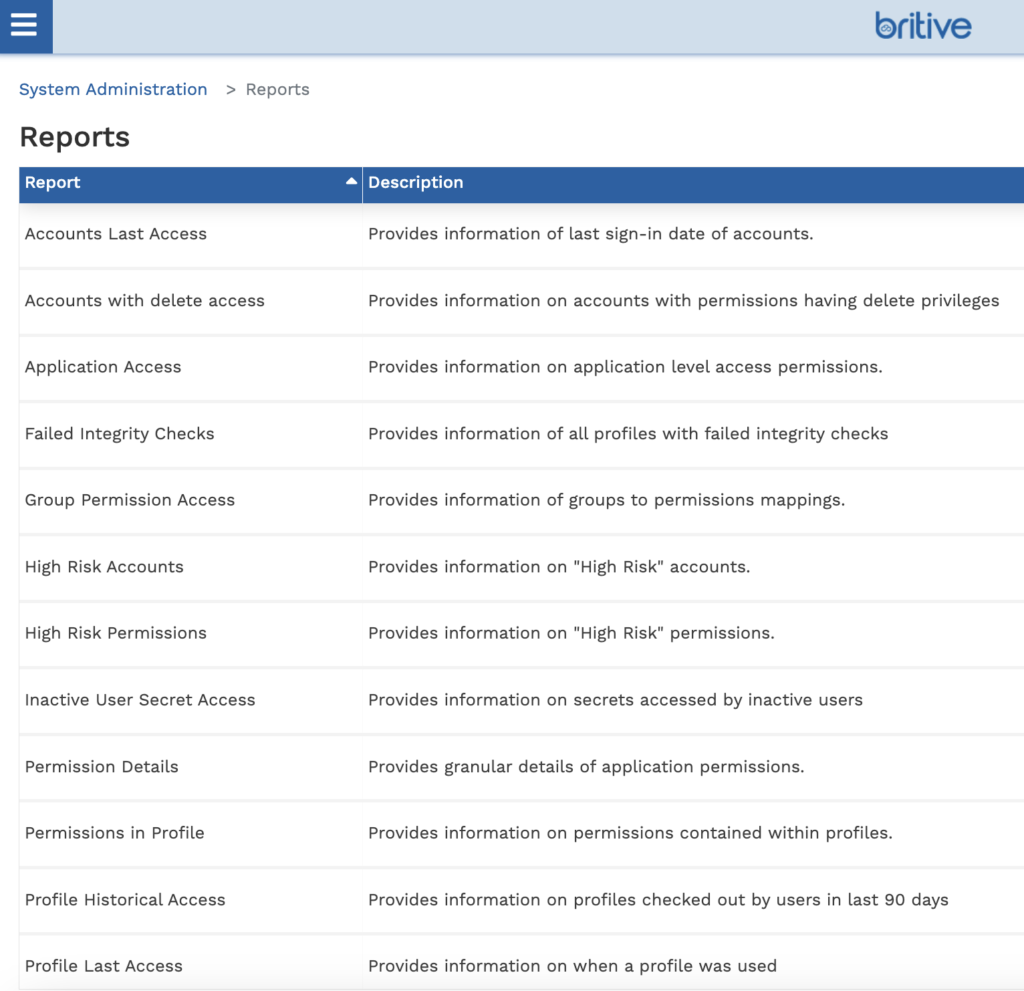
- Accounts Last Access: Provides information of last sign-in date of accounts.
- Accounts with Delete Access: Provides information on accounts with permissions having delete privileges.
- Application Access: Provides information on application level access permissions.
- Failed Integrity Checks: Provides information of all profiles with failed integrity checks.
- Group Permission Access: Provides information of groups to permissions mappings.
- High Risk Accounts: Provides information on “High Risk” accounts.
- High Risk Permissions: Provides information on “High Risk” permissions.
- Inactive User Secret Access: Provides information on secrets accessed by inactive users.
- Permission Details: Provides granular details of application permissions.
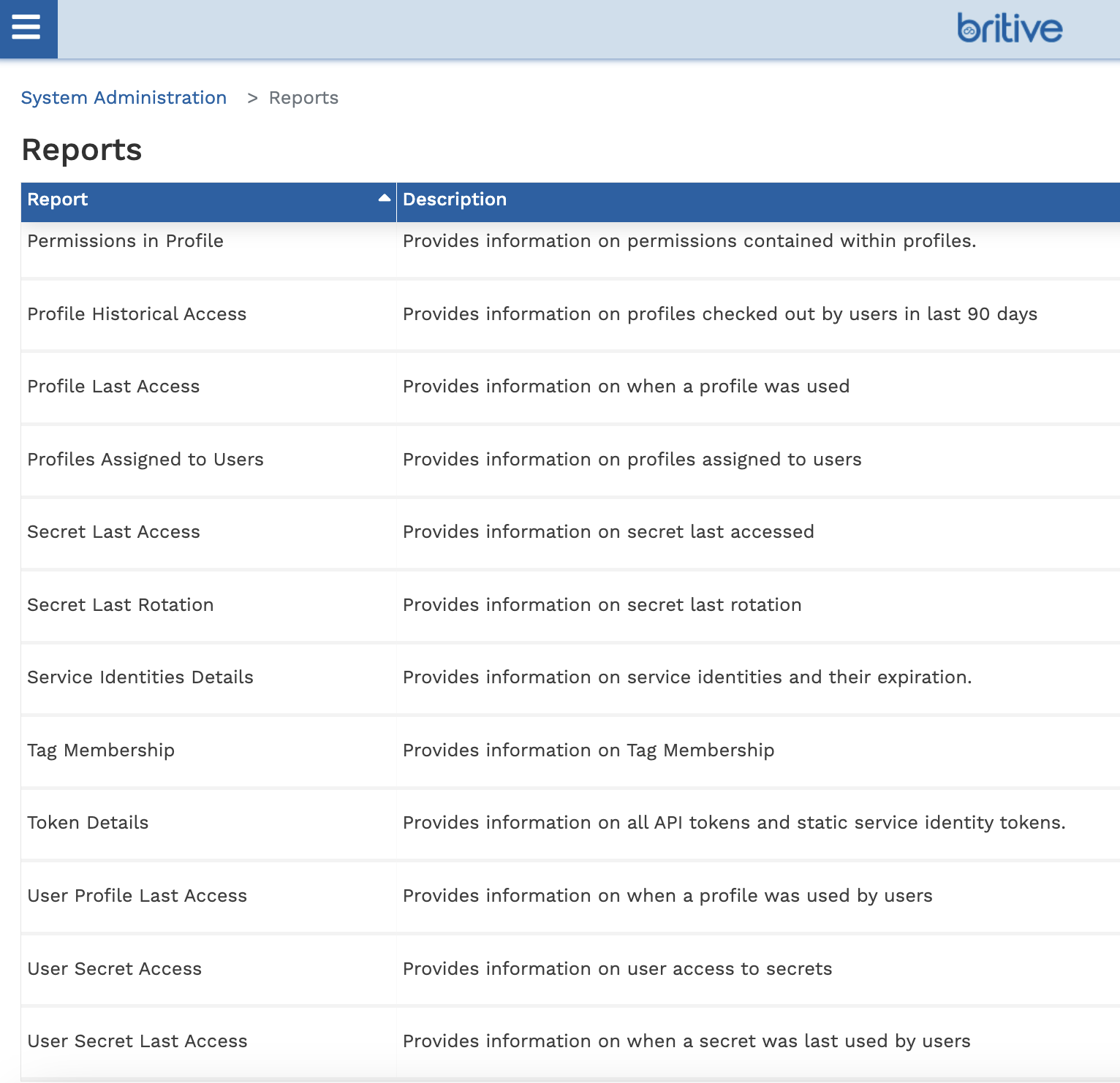
- Permissions in Profile: Provides information on permissions contained within profiles.
- Profile Historical Access: Provides information on profiles checked out by users in last 90 days.
- Profile Last Access: Provides information on when a profile was used.
- Profiles Assigned to Users: Provides information on profiles assigned to users.
- Secret Last Access: Provides information on secret last accessed.
- Secret Last Rotation: Provides information on secret last rotation.
- Service Identities Details: Provides information on service identities and their expiration.
- Tag Membership: Provides information on Tag Membership.
- Token Details: Provides information on all API tokens and static service identity tokens.
- User Profile Last Access: Provides information on when a profile was used by users.
- User Secret Access: Provides information on user access to secrets.
- User Secret Last Access: Provides information on when a secret was last used by users.
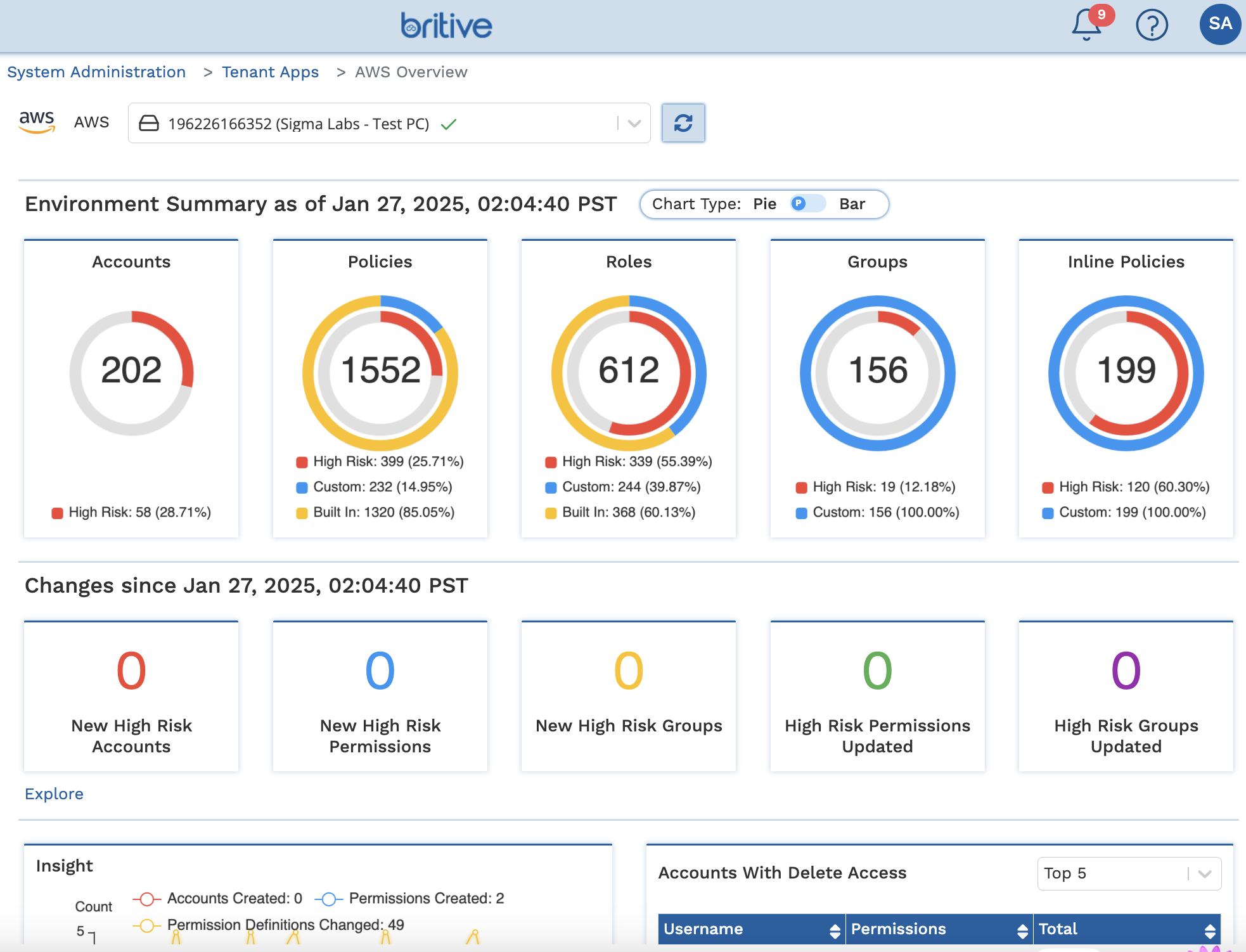
+++
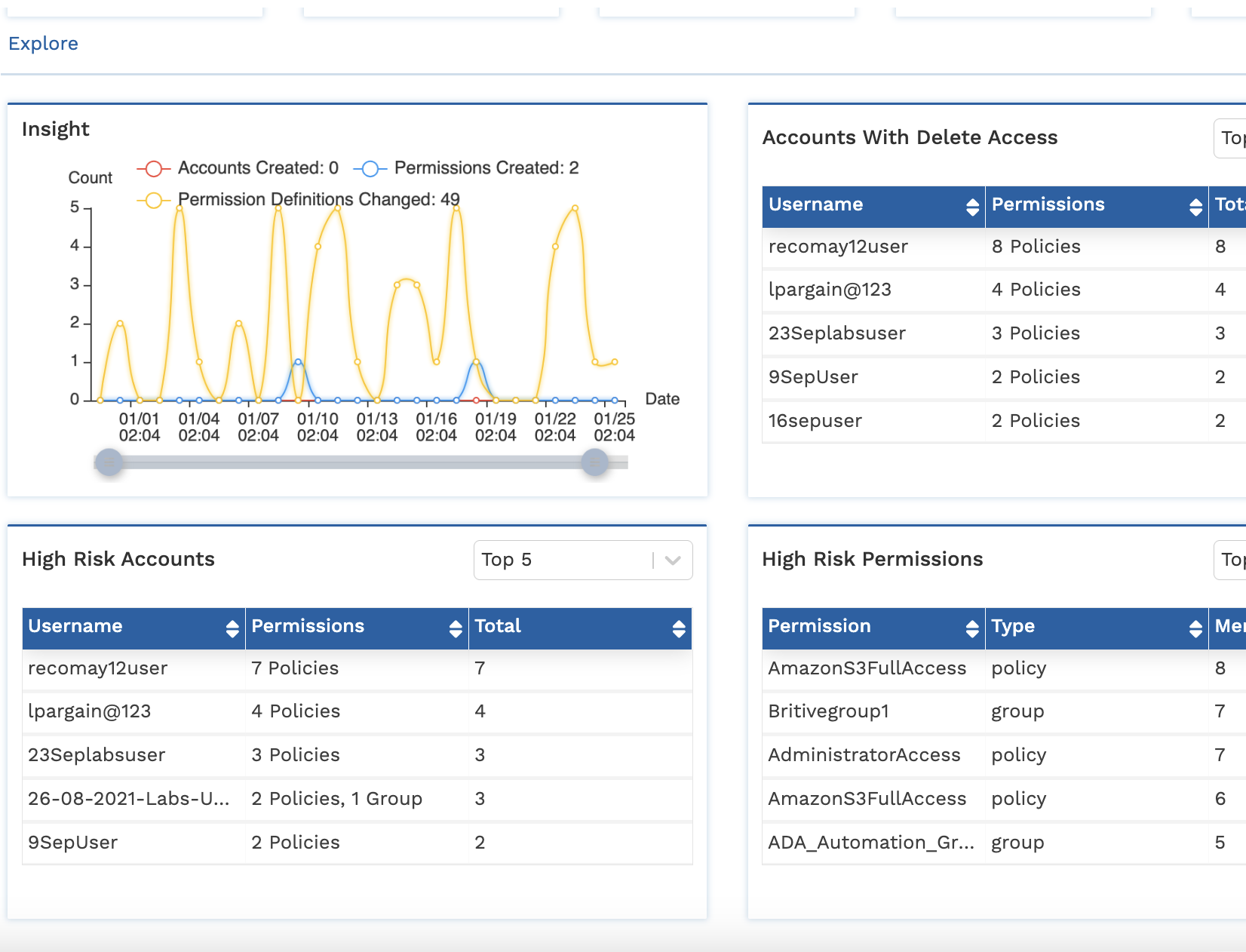
However, Britive does not stop at just showing the issues like a CIEM would. Britive tackles the root cause of privilege management issues by the enforcement of Zero Standing Privilege (ZSP) policies.
Britive Advantages are far better than CIEM Tool
Britive’s cloud-native, multi-cloud Privileged Access Management (CPAM) platform introduces an innovative approach with ephemeral, time-bound entitlements and permissions for both human and non-human identities. The platform seamlessly operates across cloud, hybrid, and on-premises environments, making it a comprehensive solution for modern access management needs.
Comments are closed