Introduction
GCP shared VPC allows an organization to share or extend its vpc-network (you can also call it subnet) from one project (called host) to another project (called service/tenant).
When you use Shared VPC in a project call “X”, you are automatically designating this project “X” as a host project. Now you can attach one or more service projects to host project “X”. The VPC networks in the host project are called Shared VPC networks. Eligible resources from service projects can use subnets you create in the Shared VPC network.
Is Shared VPC a replacement of Transit (Hub-Spoke) Network?
Shared VPC is not a replacement for transit network. Shared VPC is a management and subnet allocation concept. It does not provide enterprise grade routing or traffic engineering capabilities. Shared VPC lets organization administrators delegate administrative responsibilities, such as creating and managing instances, to Service Project Admins while maintaining centralized control over network resources like subnets, routes, and firewalls.
Aviatrix Transit Network Design Patterns with GCP Shared VPC
Aviatrix supports the GCP Shared VPC model and builds the single-cloud and multi-cloud transit networking architecture to provide enterprise grade routing, service insertion, hybrid connectivity and traffic engineering for the workload VMs. There are number of different deployment model possible but we will focus on one design with GCP Shared VPC network that is very popular among enterprises. Here Aviatrix Spoke GW is deployed in non-shared vpc subnet while the workload VMs are deployed in a shared vpc subnet.
For the other design options please check my previous blog.
Design Highlights
- Selected subnets (Prod and Dev) are shared with the service project
- Local vpcnet-transit is the VPC with only one subnet called transit-gw-subnet (10.21.4.0).
- This is the subnet we will use to deploy Aviatrix tranist GW
- As a best practice, there should not be any workload deployed inside this VPC beside Aviatrix Transit GW
- Shared VPC Prod contains two subnets in our example
- 10.21.5.0/24 is for the Aviatrix Spoke GW. This subnet is not shared
- 10.21.51.0/24 is the subnet shared with the “Prod Service Project”. This is where the workload/app VMs are deployed
- Similarly a Shared VPC Dev is created with two subnets
- 10.21.6.0/24 is for Aviatrix Spoke GW. This subnet is not shared
- 10.21.61.0/24 is the subnet shared with the “Dev Service Project”. This is where the workload/app VMs are deployed
Following diagram shows what we described above

Now let us take a look at the deployment aspects
GCP Shared VPC Subnet Settings
In GCP we are only sharing two subnets from the Shared VPC to the service project. This is the best practice as it gives centralized IT more control over what is shared and what is not. Another option is to share the entire VPC and all its subnets to the service project. These shared subnets are the ones where workload VMs will be deployed.

Transit Gateway
Transit GW is deployed on the 10.21.4.0/24 subnet in the host-project VPC. This subnet is not shared and stays local to the host-project.

Following diagram shows the GCP VPC route table where this Transit GW is being deployed

Deploy Production Spoke Gateway
Use the Multi-Cloud Transit workflow to deploy spoke gateway in production VPC. This subnet is not shared with the service project.

Deploy Development Spoke Gateway
Use the same workflow as before to deploy the spoke GW in development VPC. This subnet is not shared with the service project.

Attach Spoke GWs to Transit GW
Now attach Prod and Dev spoke GWs to Transit GW


Now the spokes are attached to the transit gw and can be seen in the following diagram

Production VPC Routing Table
Name: Global
Route Table ID: Global
| Name | Route | Target | Gateway | Priority | Tags | Status |
|---|---|---|---|---|---|---|
| avx-12a554b6a0fc446e9562c03aff9f2ff2 | 0.0.0.0/0 | default-internet-gateway | 1000 | avx-host-project-shared-vpcnet-prod-gbl | active | |
| avx-3e231ce7099947bca4f6f68a645731d0 | 10.0.0.0/8 | Instance gcp-spk-gw-host-project-prod-spk-subnet (zone us-east4-c) | gcp-spk-gw-host-project-prod-spk-subnet | 1000 | active | |
| avx-95ef9a0df3f24863a6cec71e51f2732b | 172.16.0.0/12 | Instance gcp-spk-gw-host-project-prod-spk-subnet (zone us-east4-c) | gcp-spk-gw-host-project-prod-spk-subnet | 1000 | active | |
| avx-cf9d16a2e4ec4c98908aaabd92ff7208 | 192.168.0.0/16 | Instance gcp-spk-gw-host-project-prod-spk-subnet (zone us-east4-c) | gcp-spk-gw-host-project-prod-spk-subnet | 1000 | active | |
| default-route-29758d3f2ac8689f | 10.21.51.0/24 | Virtual network host-project-shared-vpcnet-prod | 0 | active | ||
| default-route-3bfe90157ff7a563 | 0.0.0.0/0 | default-internet-gateway | 1000 | active | ||
| default-route-fc0595ff4c43a6dc | 10.21.5.0/24 | Virtual network host-project-shared-vpcnet-prod | 0 | active |
Production Spoke GW Routing Table
Name: gcp-spk-gw-host-project-prod-spk-subnet
| Destination | Via | Dev | Nexthop IP | Nexthop Gateway | Status | Metric | Weight |
|---|---|---|---|---|---|---|---|
| default | 10.21.5.1 | eth0 | up | 0 | |||
| 10.21.4.0/24 | tun-23F57229-0 | 35.245.114.41 | gcp-transit-gw-host-project-local-vpcnet | up | 100 | ||
| 10.21.4.3 | tun-23F57229-0 | 35.245.114.41 | gcp-transit-gw-host-project-local-vpcnet | up | 100 | ||
| 10.21.5.0/24 | 10.21.5.1 | eth0 | up | 0 | |||
| 10.21.5.1 | eth0 | up | 0 | ||||
| 10.21.6.0/24 | tun-23F57229-0 | 35.245.114.41 | gcp-transit-gw-host-project-local-vpcnet | up | 100 | ||
| 10.21.51.0/24 | 10.21.5.1 | eth0 | up | 0 | |||
| 10.21.61.0/24 | tun-23F57229-0 | 35.245.114.41 | gcp-transit-gw-host-project-local-vpcnet | up | 100 | ||
| 169.254.0.0/16 | eth0 | up | 0 |
Transit Gateway Routing Table
Name: gcp-transit-gw-host-project-local-vpcnet
| Destination | Via | Dev | Nexthop IP | Nexthop Gateway | Status | Metric | Weight |
|---|---|---|---|---|---|---|---|
| default | 10.21.4.1 | eth0 | up | 0 | |||
| 10.21.4.0/24 | 10.21.4.1 | eth0 | up | 0 | |||
| 10.21.4.1 | eth0 | up | 0 | ||||
| 10.21.5.0/24 | tun-23ECF407-0 | 35.236.244.7 | gcp-spk-gw-host-project-prod-spk-subnet | up | 100 | ||
| 10.21.5.2 | tun-23ECF407-0 | 35.236.244.7 | gcp-spk-gw-host-project-prod-spk-subnet | up | 100 | ||
| 10.21.6.0/24 | tun-2256383A-0 | 34.86.56.58 | gcp-spk-gw-host-project-dev-spk-subnet | up | 100 | ||
| 10.21.6.2 | tun-2256383A-0 | 34.86.56.58 | gcp-spk-gw-host-project-dev-spk-subnet | up | 100 | ||
| 10.21.51.0/24 | tun-23ECF407-0 | 35.236.244.7 | gcp-spk-gw-host-project-prod-spk-subnet | up | 100 | ||
| 10.21.61.0/24 | tun-2256383A-0 | 34.86.56.58 | gcp-spk-gw-host-project-dev-spk-subnet | up | 100 | ||
| 169.254.0.0/16 | eth0 | up | 0 |
Transit GW Route Info DB Details
{
"gateway name": "gcp-transit-gw-host-project-local-vpcnet",
"segmentation": "disabled",
"main": {
"Duplicated CIDRs": [],
"Best Route DB": {
"10.21.6.0/24": "{'type': 'vpc', 'table_id': 'main', 'as_path': '', 'as_path_len': '0', 'metric': '50', 'nexthop': '34.86.56.58', 'name': 'gcp-spk-gw-host-project-dev-spk-subnet', 'cidr': '10.21.6.0/24', 'locprf': '0', 'community': ''}",
"10.21.61.0/24": "{'type': 'vpc', 'table_id': 'main', 'as_path': '', 'as_path_len': '0', 'metric': '50', 'nexthop': '34.86.56.58', 'name': 'gcp-spk-gw-host-project-dev-spk-subnet', 'cidr': '10.21.61.0/24', 'locprf': '0', 'community': ''}",
"10.21.5.0/24": "{'type': 'vpc', 'table_id': 'main', 'as_path': '', 'as_path_len': '0', 'metric': '50', 'nexthop': '35.236.244.7', 'name': 'gcp-spk-gw-host-project-prod-spk-subnet', 'cidr': '10.21.5.0/24', 'locprf': '0', 'community': ''}",
"10.21.51.0/24": "{'type': 'vpc', 'table_id': 'main', 'as_path': '', 'as_path_len': '0', 'metric': '50', 'nexthop': '35.236.244.7', 'name': 'gcp-spk-gw-host-project-prod-spk-subnet', 'cidr': '10.21.51.0/24', 'locprf': '0', 'community': ''}"
},
"Route Info DB": {
"10.21.6.0/24": [
"{'type': 'vpc', 'table_id': 'main', 'as_path': '', 'as_path_len': '0', 'metric': '50', 'nexthop': '34.86.56.58', 'name': 'gcp-spk-gw-host-project-dev-spk-subnet', 'cidr': '10.21.6.0/24', 'locprf': '0', 'community': ''}"
],
"10.21.61.0/24": [
"{'type': 'vpc', 'table_id': 'main', 'as_path': '', 'as_path_len': '0', 'metric': '50', 'nexthop': '34.86.56.58', 'name': 'gcp-spk-gw-host-project-dev-spk-subnet', 'cidr': '10.21.61.0/24', 'locprf': '0', 'community': ''}"
],
"10.21.5.0/24": [
"{'type': 'vpc', 'table_id': 'main', 'as_path': '', 'as_path_len': '0', 'metric': '50', 'nexthop': '35.236.244.7', 'name': 'gcp-spk-gw-host-project-prod-spk-subnet', 'cidr': '10.21.5.0/24', 'locprf': '0', 'community': ''}"
],
"10.21.51.0/24": [
"{'type': 'vpc', 'table_id': 'main', 'as_path': '', 'as_path_len': '0', 'metric': '50', 'nexthop': '35.236.244.7', 'name': 'gcp-spk-gw-host-project-prod-spk-subnet', 'cidr': '10.21.51.0/24', 'locprf': '0', 'community': ''}"
]
},
"Best Route DB (linklocal)": {
"10.21.4.0/24": "{'type': 'linklocal', 'table_id': 'main', 'as_path': '', 'as_path_len': '0', 'metric': '0', 'nexthop': '', 'name': 'gcp-transit-gw-host-project-local-vpcnet', 'cidr': '10.21.4.0/24', 'locprf': '0', 'community': ''}",
"10.21.4.3/32": "{'type': 'linklocal', 'table_id': 'main', 'as_path': '', 'as_path_len': '0', 'metric': '0', 'nexthop': '', 'name': 'gcp-transit-gw-host-project-local-vpcnet', 'cidr': '10.21.4.3/32', 'locprf': '0', 'community': ''}",
"10.21.6.2/32": "{'type': 'linklocal', 'table_id': 'main', 'as_path': '', 'as_path_len': '0', 'metric': '0', 'nexthop': '', 'name': 'gcp-spk-gw-host-project-dev-spk-subnet', 'cidr': '10.21.6.2/32', 'locprf': '0', 'community': ''}",
"10.21.5.2/32": "{'type': 'linklocal', 'table_id': 'main', 'as_path': '', 'as_path_len': '0', 'metric': '0', 'nexthop': '', 'name': 'gcp-spk-gw-host-project-prod-spk-subnet', 'cidr': '10.21.5.2/32', 'locprf': '0', 'community': ''}"
}
Note: Aviatrix UserConnect-6.2.1528 was used to validate this design.
Validation
Transit and spoke VMs deployed successfully in the host project
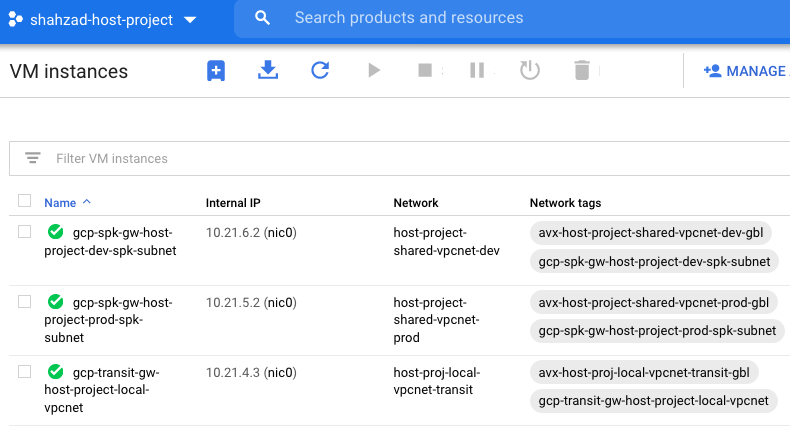
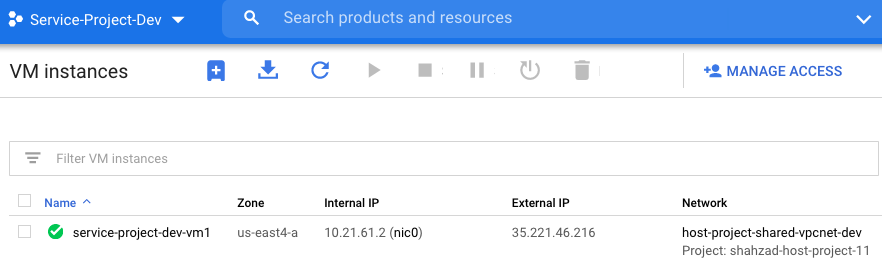
Workload VMs were deployed in their respective service projects on their respective shared subnets

For validation ssh was enabled on the dev workload VM and ICMP was also enabled. From Prod VM both ICMP and ssh were successful

ssh was also successful as we can see from the following

Comments are closed