I wanted to share some resources that detail the implementation and design aspects of Britive K8S […]
I use Video Format Conversion HandBrake is an amazing app. Works great on Mac. HandBrake is […]
The rapid evolution of artificial intelligence (AI) is fundamentally reshaping the cyber threat landscape, arming adversaries […]
AI governance and compliance mapping is becoming critical as organizations scale their AI deployments. Let me […]
This content presented in this blog is originally published here –> https://docs.britive.com/docs/prerequisites-aws-onboarding. For the latest information […]
Introduction As organizations accelerate their cloud adoption, managing access to critical AWS resources has become increasingly […]
Abstract Agentic AI is shifting from experiments to production, and the Model Context Protocol (MCP) is quickly becoming […]
Executive Summary Britive Access Builder is a powerful self-service capability that transforms how organizations manage cloud […]
Setup Total Duration: ~5 minutesNumber of Scenes: 7Target Scene Length: 60-80 seconds each Scene 1: Introduction to Britive Access […]
Introduction (0:00 – 0:30) “Hello everyone, and welcome to this demonstration of Britive’s dynamic credential management […]
https://aws.amazon.com/startups/events/aws-britive-building-secure-compliant-agentic-ai Replay is here: https://www.linkedin.com/events/7383969595780657153 Youtube is here: https://www.youtube.com/watch?v=zaOVOIepQQQ Join Amazon Web Services (AWS) + Britive for a […]
Why Jeff Bezos refused to add color to the Kindle. What every founder must learn from […]
TL;DR Key Pain Points in K8s Access Management How A Modern PAM Solves These for K8s […]
If you get above error, you must view the CloudWatch logs to know exactly the issue. […]
A practical, step-by-step resource that helps organizations understand how to adopt and implement a new solution, […]
Hey everyone. Today, we’re diving into a topic that’s reshaping enterprise identity and access management: the […]
Understanding IAM Conditions in Google Kubernetes Engine (GKE) Think of IAM Conditions in GKE like access control […]
Before we start the demo quick Kubernetes RBAC primer. PAM Solution The PAM solution relies heavily […]
For this configuration, we will save the Windows PowerShell script in the UI itself. The other […]
1- Settings –> Data Collection –> Collection 2- Add Collector 3- Hosted Collector Add HTTP Source […]
An Apache Guacamole RDP connection looks like following. This is also called Guacamole remote desktop session launch […]
Amazon Bedrock AgentCore announced in July 2025. It is designed to simplify the deployment of AI […]
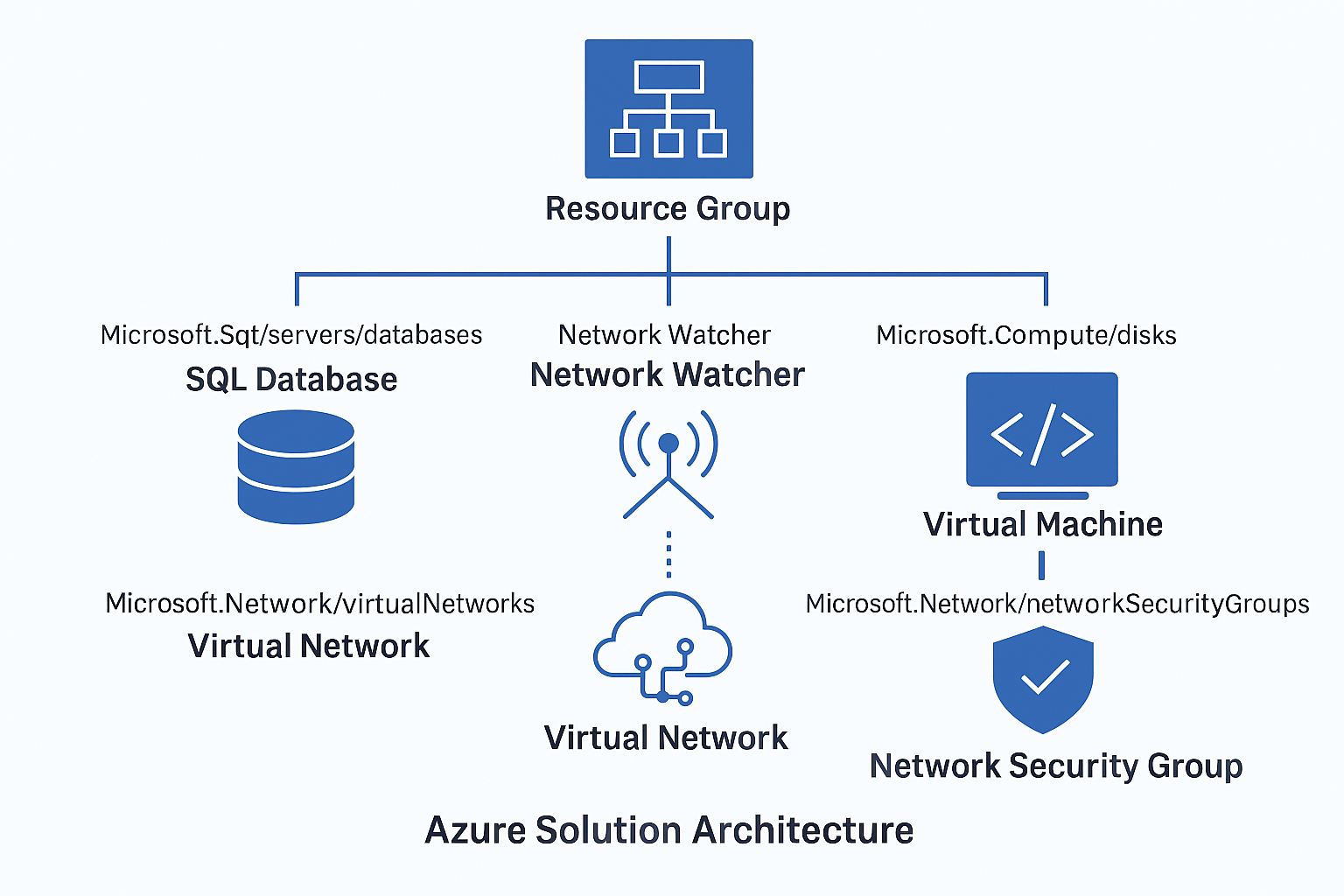
🔹Resource Group 🔹 Specific Resource Types (e.g., Microsoft.Sql/servers/databases) 🔐 1. Resource Group (e.g., sql_demo_rg, Win-Servers) 🗄️ 2. Microsoft.Sql/servers/databases 3. Microsoft.Network/networkWatchers 🧠 4. […]
Q: Can AWS Bedrock agent talk to another AWS Bedrock agent? Yes, Amazon Bedrock agents can […]
Within the realm of Amazon Web Services’ generative AI platform Amazon Bedrock, an action group is a technical concept […]
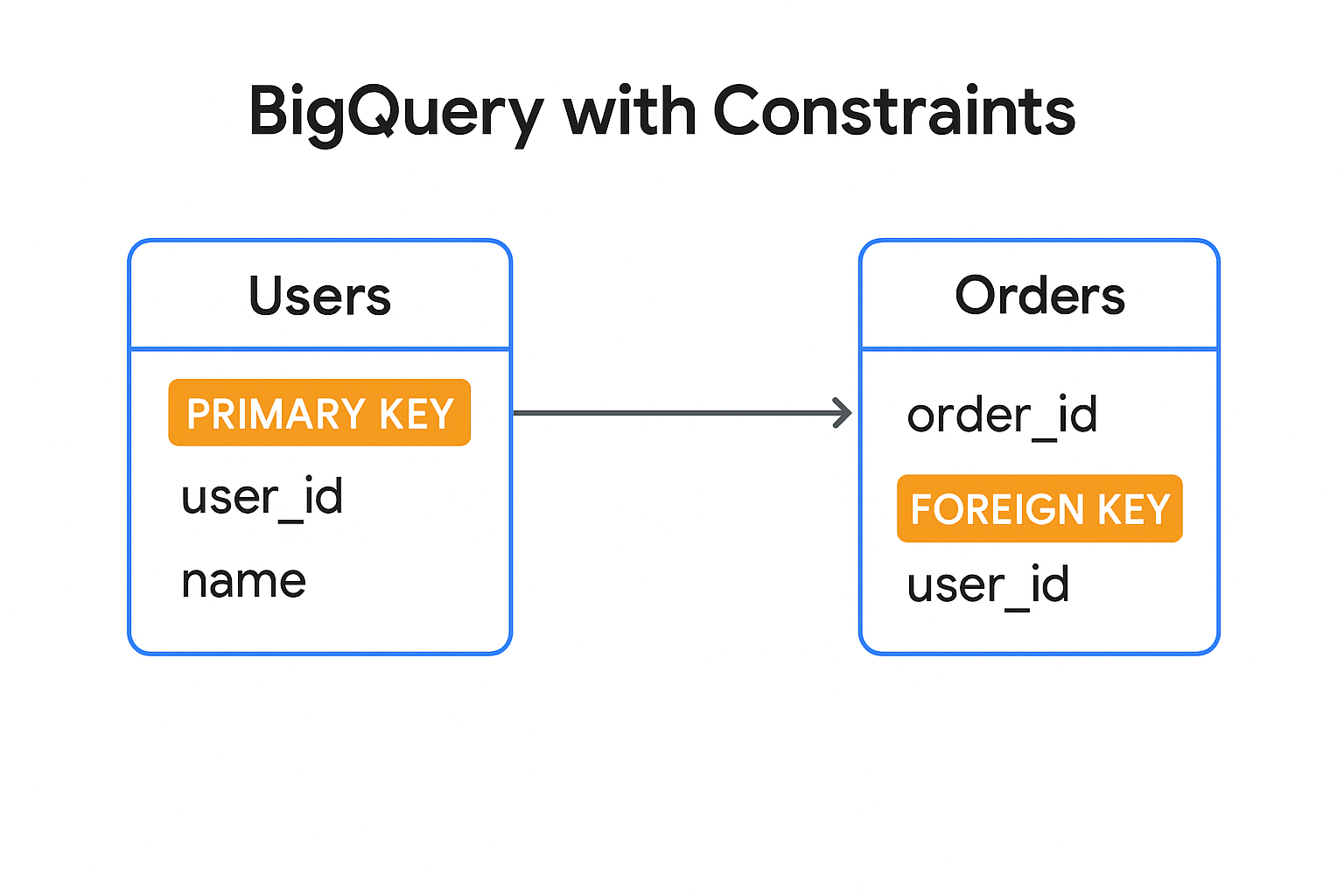
What is BigQuery? BigQuery is a tool in GCP that lets you store and analyze large amounts […]
Today, we’re discussing GCP’s super useful tools called Pub/Sub. Now, that might sound a little complicated, […]
GCP Shared Service Account Pain Point Circumvention of Security Protocols: One of the pain points in […]
Amazon announce this new capability in July 2025. Amazon Bedrock AgentCore helps you build and run […]
The difference between Amazon Aurora, Amazon RDS, and MySQL can be understood by looking at three levels: database engine, database service, and deployment […]
Azure PIM (Privilege Identity Management) is a valuable tool, but can it truly meet the comprehensive […]