Problem Statement
By default GCP Compute Service Account permissions are wide open with the Editor role. Here is how you can see the problem yourself.
Create a new GCP Project
Notice the “Service Accounts” area and notice that there is no account there yet.

Enable Compute API for PCI Service Project

Default GCP Service Account
A default Compute Engine GCP service account (845482233226-compute@developer.gserviceaccount.com) is created as you can see from the following diagram

More details about this default compute engine service account can be seen in the following diagram
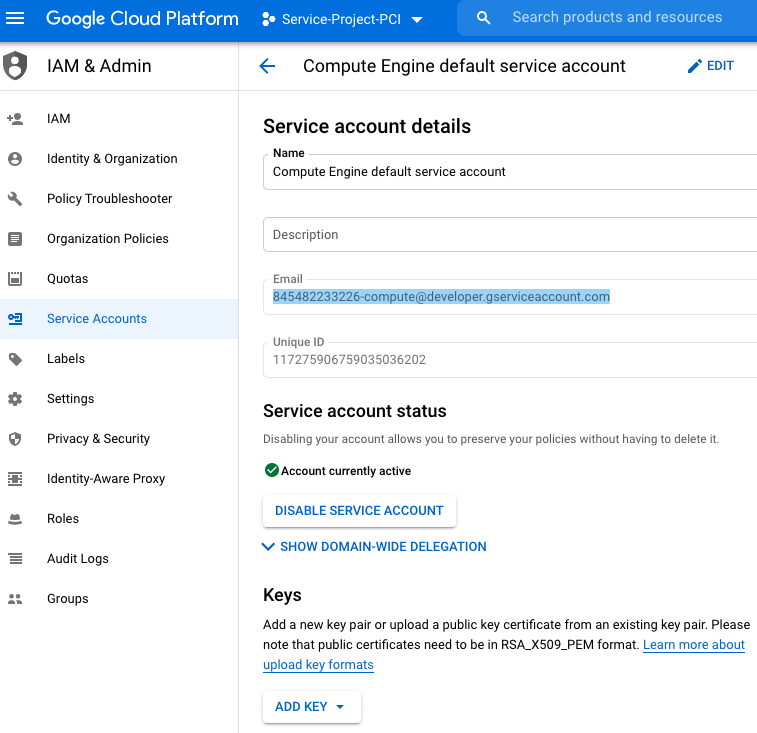
IAM Permissions For Default Compute Account
If you go back to IAM area, notice the the default compute account is there. By default it comes with “Editor” permission. Editor is a wide open permission and should not be used in production for a service account

How to Fix this Problem?
The fix is not difficult. There is an automated way and a manual way. I will explain the manual method and have provided URL for the automated way as well.
Change the permission on GCP Default Compute Service Account
When a VM (such as Aviatrix Egress FDQN, User-VPN, Transit, Spoke GW etc.) is deployed in the GCP Project, the GCP project automatically associates a Default Service Account with it. It is the default GCP behavior and cannot be changed. Notice that this account is different than the account we created to on-board the GCP project into Aviatrix Controller
There are two methods to restrict the permission for the default service account
1- Automated Method: Global IAM setting to disable automatic role grant for Default Service Account
2- Manual Method: Change the permission for Default Service Account
1- Automated Method: Global IAM Setting to disable automatic role grant
GCP recommends production customers to disable automatic role grant to default service accounts
https://cloud.google.com/iam/docs/service-accounts
“When a default service account is created, it is automatically granted the Editor role (roles/editor) on your project. This role includes a very large number of permissions. To follow the principle of least privilege, we strongly recommend that you disable the automatic role grant by adding a constraint to your organization policy, or by revoking the Editor role manually.”
Some Google Cloud services automatically create default service accounts. When a default service account is created, it is automatically granted the Editor role (roles/editor) on your project.
To improve security, we strongly recommend that you disable the automatic role grant. Use the iam.automaticIamGrantsForDefaultServiceAccounts boolean constraint to disable the automatic role grant.
2- Manual Method: Change the permission for Default Service Account
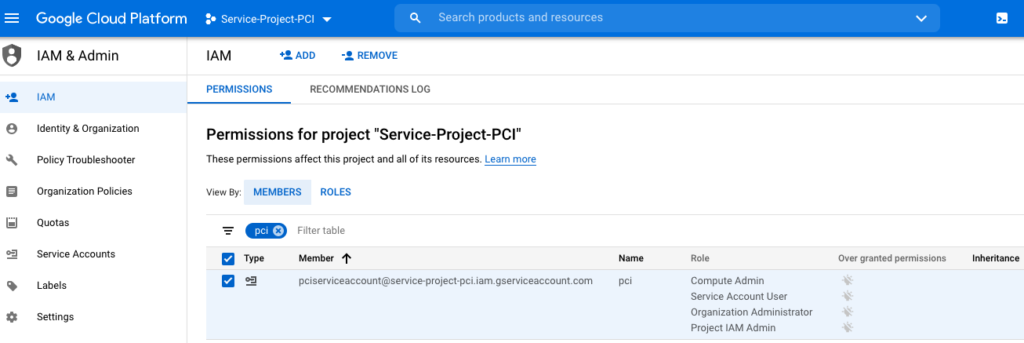
In my setup I used the manual method to change the permission for default service account. I assigned the least possible access role to this new member PCI. Aviatrix at minimum would need
- Compute Admin
- Service Account User
- Organization Admin and
- Project IAM Admin role.
Note: Organization Admin and Project IAM Admin roles are only needed for “Shared VPC”. Skip those roles if you are not planning to use “Shared VPC”
Following screen shows the example of editing the permission for a memeber

After you save, it should look like following
Now select/click this “Service Account” area under “IAM & Admin”
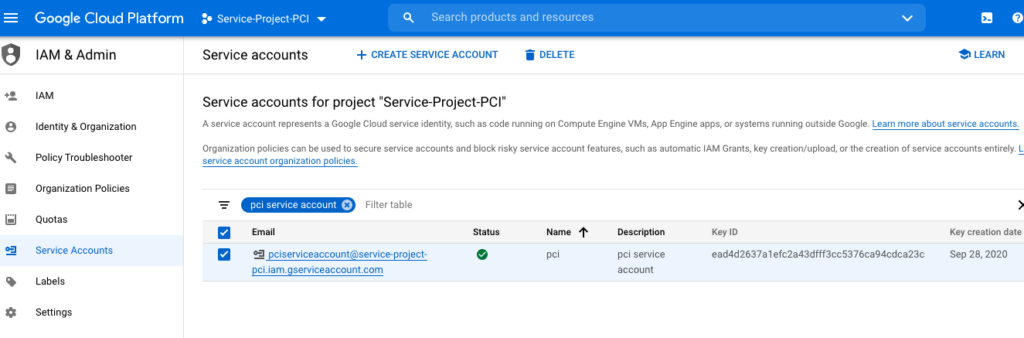
Now “Create new key” key for this service account.

The type must be Json

The new key is created and downloaded on your machine now

This Jason key is what we will use to on-board the GCP account in the Aviatrix Controller
Following is the sample of how it looks like
{
"type": "service_account",
"project_id": "service-project-pci",
"private_key_id": "746b9729f7aaeb0762e637e443941a960542124f",
"private_key": "-----BEGIN PRIVATE KEY-----\nMIIEvgIBADANBgkqhkiG9w0BAQEFAASCBKgwggSkAgEAAoIBAQC1aWbZnR+GHCrM\ncL1ETvam4Q2bb7nXbEtT8aOj6SIt3zJMIN0ycJ40W7QqBS57bBYhF/mskkOEbP60\nkfkKp1ygM5eg5q7+bXINGm5rpDu0VvK7BWvA+lKOGpvJSA3SOEMN+kvr5p3H+iRl\ngE802d0OzR981bWGRodqan3+i3u52K5b4c/25e2nxq0WvTGD+/LcIYZKVTx6PM1X\nfuPNaHhKIk8lMt7HOlT/Y+CJ9/qdPtct/sZak6B0BM5AiurIBYV4Pk87PuhIF+W8\nz0WGtDQ50YvrRWOK6qKFOcs6Z1lZDx1bIUDfj80ItIDw64z9f1wHNC1SEuOHqaJ+\nItFrvBCzAgMBAAECggEAMjL7ceZHrd2nf0xjIz7Sg/UsxcFR5Kmj4pOwG5BMk/L6\nQRSrAOUm8ggaP7J1XVPYf8nZngZPRpq+lIr8JhWPzQjZwX10GRWCBNw2h/THTKzu\nuA/U9G6QX6A/UaBtqqlE7N5BGgMT0B2I6slpoY9T21+pgerFM2Xa3Pig6soAL7mt\nbPY7soSVFshf0EcV3ZkYTxuBXaDdJtLftoimsyJBFYomWHg3WTF/Gp2ua5XC27U1\nDhQ6bR2urQcbcusL+xMeS5ZBo1HyBzJKkQSuHixG7OY62VTct8o89vWIg18oSUaA\nqvcD3WIjh1jNDVHx2JgE1b5INvoLHVZoPGDlZOCa6QKBgQDlgsrBygZLEdtvI9IG\nXcRqIgMI+H3XbIZKYYA4G1Qo+ummsMzIWJyOjotEfanh3SNt/nabUyQjvTezsOHS\n2xvU+R+ISi6GhNLrF+zzvktgwOA8IoCn21gWRLsad4ergDAYDZ6B7q2KWLP9O+DE\nyiN5o/l9l+PATUy7XYaHkhhQVwKBgQDKWXRwmRXnZc3Jb/2sTeJp77i0N163mKVL\n0RNONMFJ2W5i7+Fz9hQ4o/bnGdcPtZbncDHlXCkJEBqx0UfKd6IAW16tvF+gS9OV\n9j9JrqCgaT44mOduMSWkyIqOP4L7Wpp49y36xkfXzkbkmaDShrQpc+KHydmBrNM0\nMQpCD6YZBQKBgQCmQRKDQsdARhVA8x/HANGxWCX+r5LpJHI7G1n4SsOyU+BBob0W\nPCpckiGMYcNYHAr4OObOKXH6ea0J+836IkKNClGvNp1xUHJBXrmE74pG8jD9Hrk3\n3wp2Rx+KUp/yug8cvXDfCninyQ3JGUD/DLaZ/RBTzF1tBhHZgCxdtJTsTQKBgHQM\njb0t7uQA/N60PdYd7OY4t8OTpdzBzLsIs3u8wcXqz2YqkTCCRuKdFrM/nJnD2UHu\nlI8oJdiuxcCJeBTkO6LcxBX73RP/qN9ulKlbX3/gG/E1sDUANsikwuIGBsbFFaae\njF4wbW+VPA9LFHLpElZbweWCnB3E0nQyU+HDO81JAoGBAJ+FLYEqEDwHeskO/us7\nR4pG0A55QpGduQaDtJcW2rQZXhwLOZklucUWVtilUiOGQt9Kk3v31n9R4zhfyS2c\n+RfIs1fHgvEzBhrEUxKchvkcVOSwIOqklk1+wjXvIVlb5zLklyV+cIqaDi7wp26g\nOwMtNj72PO+5w28/4b0rnqTW\n-----END PRIVATE KEY-----\n",
"client_email": "pciserviceaccount@service-project-pci.iam.gserviceaccount.com",
"client_id": "106577340982754556535",
"auth_uri": "https://accounts.google.com/o/oauth2/auth",
"token_uri": "https://oauth2.googleapis.com/token",
"auth_provider_x509_cert_url": "https://www.googleapis.com/oauth2/v1/certs",
"client_x509_cert_url": "https://www.googleapis.com/robot/v1/metadata/x509/pciserviceaccount%40service-project-pci.iam.gserviceaccount.com"
}
Now under Aviatrix Controller –> Access Account, onboard the GCP Project as shown in the following diagram. Leave the Project ID filed blank. Controller will automatically pick the name

Following diagram shows that on-boarding GCP project was a success

Deploy Aviatrix Gateway For GCP Project
Now when I deploy the Aviatrix GW, it will be using the restricted permission to connect to GCP and then when the GW is deployed.
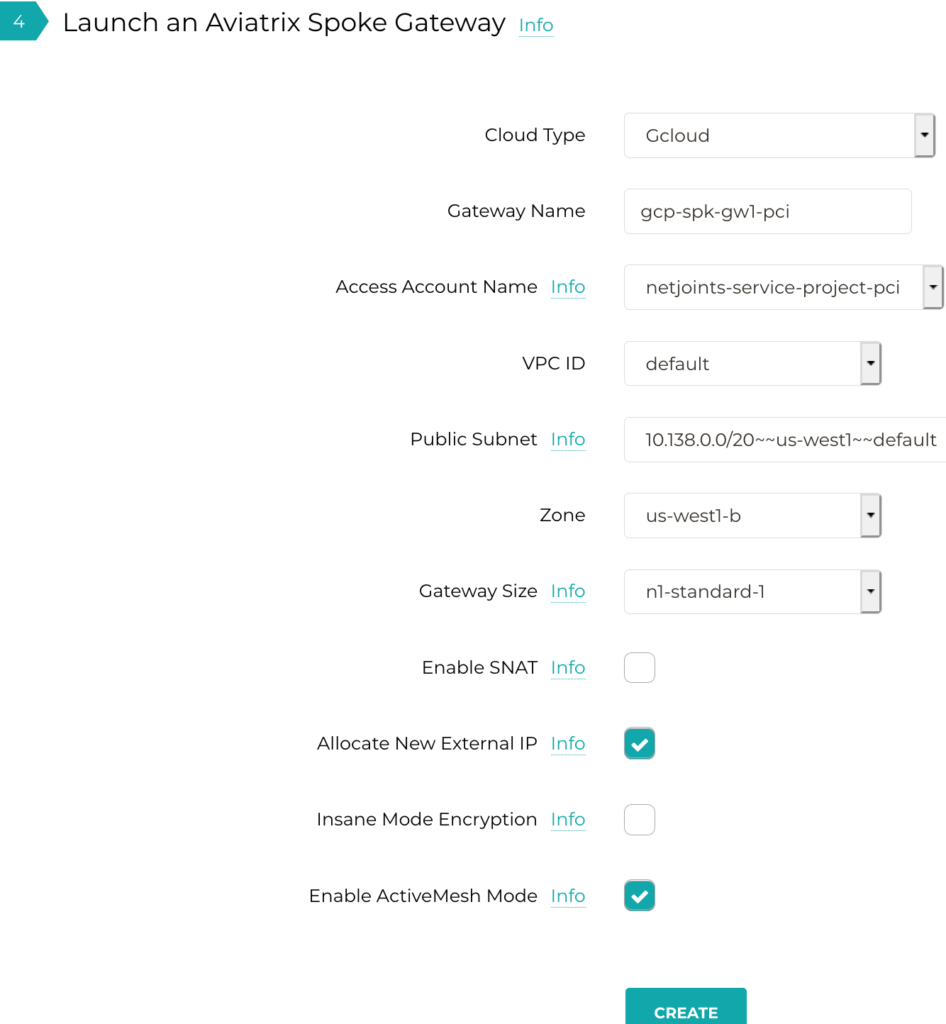
GW Deployment Progress on GCP
Controller shows the following output
[12:39:07] Starting to create GW gcp-spk-gw1-pci.
[12:39:08] Connected to GCE.
[12:39:13] Project check complete.
[12:39:14] License check is complete.
[12:39:23] Updating IGW for new gateway…
[12:39:31] Launching compute instance in GCE….
[12:40:34] GCE compute instance created successfully.
[12:40:34] Updating DB.
[12:40:34] Added GW info to Database.
[12:40:36] AVX SQS Queue created.
[12:40:36] Creating Keys.
[12:41:03] Initializing GW…..
[12:41:03] Copy configuration to GW gcp-spk-gw1-pci done.
[12:41:04] Copy new software to GW gcp-spk-gw1-pci done.
[12:41:05] Copy misc new software to GW gcp-spk-gw1-pci done.
[12:41:05] Copy scripts to GW gcp-spk-gw1-pci done.
[12:41:05] Copy sdk to GW gcp-spk-gw1-pci done.
[12:41:10] Copy libraries to GW gcp-spk-gw1-pci done.
[12:41:10] Installing software ….
[12:41:11] Issuing certificates …
[12:41:27] Issue certificates done
Instance creation can now show you following

On the GCP VM Instance notice that Aviatrix does not assign any service account or allow access to any GCP Cloud API for additional security.

Comments are closed