Aviatrix controller provides unified control and management plane for Google Cloud. Aviatrix allows enterprises to on-board hundreds of GCP projects/accounts into the controller. Once these projects are on-boarded, Aviatrix controller is intelligent to control and manage networking and security across those projects.
On the Aviatrix document page one of the options is to use the “Editor” service account to on-board the project.
https://docs.aviatrix.com/HowTos/CreateGCloudAccount.html
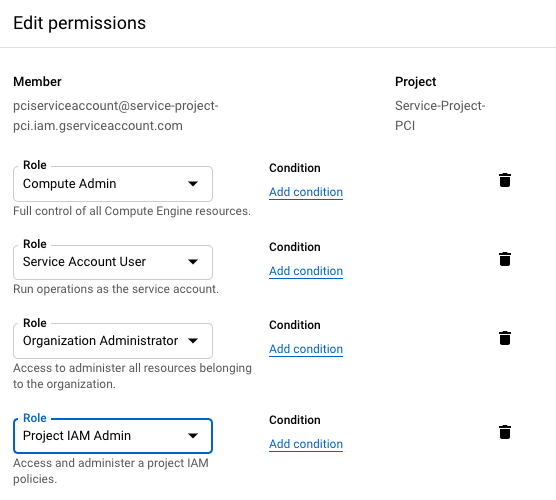
This might not be desirable for many enterprises as they would want to use least privileged service account credentials. In such a situation Aviatrix recommendation is to have at least following roles assigned to service account so that Aviatrix can perform its functions properly. For instance managing the compute resources, route tables, firewall rules, shared service vpc network etc.
- Compute Admin
- Service Account User
- Organization Administrator (optional and required for Shared VPC)
- Project IAM Admin (optional and required for Shared VPC)
Comments are closed